Disrupt or be disrupted: This could be more or less the motto of digital transformation. There are no longer any areas that remain unaffected – not even in cyber security. For many, "digitalisation" has become a buzzword, but if you take a look at the status of some web-based technologies, it is obvious that there is still a lot to do. In this article, we explain how Web Application Firewalls (WAFs) have adapted to digitalisation.
The discussion around digitalisation has long since ceased to be about "why", now it’s about "how", and so today it's all about operational implementation. It probably goes without saying that there is no single solution. This makes it all the more important that technologies do justice to digitalisation and that the resources needed for change are made available. That's all very well, but what about IT security and more specifically Web Application Firewalls (WAF)?
Digitalisation with integrated IT security solutions
Due to digitalisation, applications, APIs, data and identities are increasingly being exposed beyond the boundaries of enterprise IT. For example, these days not only websites communicate with internal IT, but also external APIs are communicating with customer identities or IoT devices. As a result, IT security solutions must be capable of adapting to increasingly complex situations and must be easily scalable. Here, the trend is towards an integrated IT security solution. Here the advantage is that application security, API protection and access management converge.
WAFs, API and IAM as an integrated solution
However, there are always challenges to overcome as well as benefits, because WAFs need to protect APIs and APIs need to learn web security. In addition, APIs require access control and users are finding it hard to manage with traditional enterprise IAM systems. So how can this problem be solved? Fairly simply in fact. It can be done by means of integrated systems with intelligent interfaces where individual components are matched to each other in a coherent way, and loose ends are linked to each other. In technical terms: secure access management requires a convergent solution consisting of a WAF, an API gateway and a Customer IAM System (CIAM).
5 challenges of WAF and digital transformation
As already mentioned, building a coherent safety ecosystem with converging technologies poses a number of challenges. For example, employees, customers, partners, IoT devices, etc. must also be taken into account during the planning and implementation phases. You should be ready for the following five challenges:
- WAFs need to learn more: Compared to the situation ten years ago, web application firewalls have become an integral part of corporate IT; and yet today's systems are not meeting the requirements of digitalisation – the keywords here are user experience and service networking. As a consequence, conventional web applications are dying out. Modern applications are rich clients that run in the browser and usually integrate their own and third-party services (APIs). However, these application programming interfaces do not use the same data formats as conventional web applications, so new technology is called for to protect APIs.
- API Security not without web security: API gateways are subject to new requirements that are similar to a WAF, making issues such as web security also pertinent – for example, OWASP Top 10. This is because traditional XML gateways can only provide partial security for the new web services. These usually communicate among their peers as SOAP (Simple Object Access Protocol) web services. But more and more frequently, REST (Representational State Transfer) web services are being used. These are more agile and more suited to devices with a limited profile, such as mobile devices. Web services also vary widely in other ways, so modern API gateways must be able to meet different needs in terms of digital transformation and web security.
- Access Management of APIs: API Gateways are particularly used for access control where content filtering is very important. Standards such as OAuth 2.0, SAML and OpenID Connect are used for security. User identification is also part of the technical authorisation of clients. This, in turn, requires the integration of Web Single Sign-On and Identity & Access Management (IAM).
- Identity & Access Management and clients: Identity management is very complex and includes a multitude of external identities such as customers and partners. Not only do these have to be managed, but they are also subject to regulatory requirements such as the GDPR or the Payment Services Directive PSD2. This means that access needs strong authentication. The solution here is Customer Identity & Access Management (CIAM). Compared to enterprise IAM systems, they are better designed for managing external users. They can be easily scaled and ensure a seamless user experience via integrated UIs for onboarding and self-services. The decisive factors here are dealing with social identities (BYOI; Bring Your Own Identity) and a high degree of flexibility in adaptive authentication.
- Organisational Structures – Fighting Silo Thinking: As well as the technical challenges, almost all areas have one thing in common, the organisational obstacles – above all silo thinking in companies, which is infamous. This raises new questions, demands flexibility and necessitates a rethink. For example, you need to know who the contact person and decision-maker is – is it the CISO, because it relates to security issues, or is it management because integrated solutions ensure a lower TCO and a faster time-to-market? Does marketing have to be included because of issues such as user guidance and bounce rates? There is no standard answer but there are holistic approaches, so it is becoming increasingly important in IT security to consider the situation from several different angles, because digital transformation does not just mean technical changes, it also involves changes to business processes, organisational structures, customer behaviour as well as the behaviour of employees and partners.
Airlock Secure Access Hub – integrated IT security solution from a single source
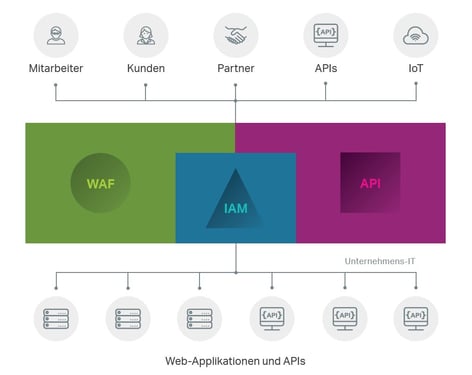 Innovative solutions are needed if we want to keep pace with the fast-moving digital transformation in these areas. Our Swiss partner and market leader, Ergon Airlock is offering a broad range of solutions in WAF, IAM and API, including "Secure Access Hub". The secure access hub brings together the three elements of access management, interface protection and applications on one platform.
Innovative solutions are needed if we want to keep pace with the fast-moving digital transformation in these areas. Our Swiss partner and market leader, Ergon Airlock is offering a broad range of solutions in WAF, IAM and API, including "Secure Access Hub". The secure access hub brings together the three elements of access management, interface protection and applications on one platform.
- The API gateway on Airlock's Secure Access Hub is a reverse proxy with failover and load balancing capabilities, providing a filtering arsenal for web security and enabling role-based access authorisation for API endpoints.
- The Airlock WAF blocks attacks before an attacker can gain access to internal systems, provides central management for security policies, ensures high levels of availability due to the integrated load balancer, and automatically processes certificate renewals using the Let's Encrypt function.
- The third component, Airlock IAM, allows for major scaling of the number of users, enabling high levels of flexibility in the authentication process and the handling of social identities. In addition, Airlock's Identity & Access Management is compatible with various solutions and can be used by means of e-mail, OTP, mobile TAN, password, etc.
The Airlock Secure Access Hub is an altogether credible solution. It not only makes your WAF fit for digital transformation but also your API and IAM. You can find out more about Airlock's Secure Access
[Whitepaper] IT Security Solutions & 7 Misconceptions about Web Application Security
If you would like to find out more about IT security solutions and the Secure Access Hub from Airlock, then download the free whitepaper "IT Security Solutions – from digitalisation killjoy to accelerator". You will not only learn more about the challenges of integrated IT security solutions but also about its advantages and best practice from Raiffeisen Bank. At the same time, you will also be given the Airlock whitepaper: "The 7 Classic Misconceptions in Web Application Security". You will learn about the frequent misjudgments and the way to do things properly. Download it now! (Whitepapers in German)
Picture source: Ergon Airlock



