Governance, risk & compliance (GRC) is the collective term for subjects and processes such as corporate management, risk management, internal control system (ICS) and compliance. It is by no means an easy matter! In my latest blog post, you can read about why you need to deal with GRC, and how to keep all these important issues under control!
These days, companies are operating in a business environment that is highly complex, highly dynamic and sometimes global. As a result, the internal demands on risk management and the internal control system are growing steadily. Pressure from regulators, shifting competition, compliance requirements, cyber crime and the growing complexity of infrastructures are just some of the major factors driving the internal and external demands being made on companies. Managing these demands and their impact on risk and compliance are two of the biggest challenges that risk managers, compliance officers, CISOs or information security officers (ISOs) – depending on the size of the company – are having to deal with.
What does GRC mean?
The term “governance, risk & compliance” (GRC) describes a company's three most important spheres of activity in terms of successful management.
GRC is a comprehensive, integrated approach to risk management, compliance and governance across an organisation. It is a means of ensuring that the organisation behaves in an ethical way, and in line with its risk appetite and internal and external guidelines. The aim of this approach is to increase efficiency and effectiveness by coordinating strategies, processes and technologies.
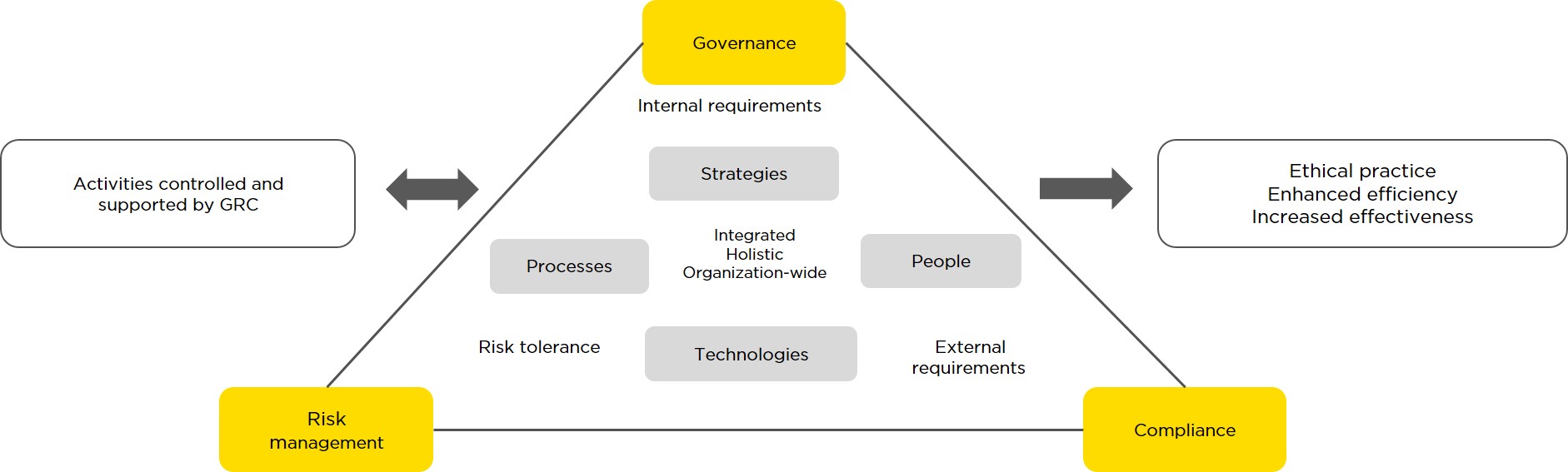
The three principal components of GRC in the IT environment
Governance
Governance ensures that organisational structures and processes – such as the management of IT operations – underpin the business strategy and objectives. IT needs to be aligned with the company's business activities in an optimal way, and in so doing, help the organisation to ensure that the IT resources provided are used to optimise the factors of cost, quality and security. Any risks arising from IT operations are also expected to be reduced or minimised. What this means in concrete terms:
- The information security policy and information security objectives must be defined and aligned with the organisation's strategic direction.
- Requirements for the Information Security Management System (ISMS) are to be integrated into the company's organisational procedures.
- The resources required for the ISMS must be made available.
- The importance of having an effective ISMS is to be communicated, and at the same time, the requirements of this system are to be met.
- It must be ensured that the ISMS achieves the desired results.
- Employees must be trained and able to provide active support themselves to promote the ISMS's effectiveness.
- The continual improvement process (CIP) must be promoted.
Risk management
Risk management (RM) is an ongoing process that includes identifying and assessing risks and planning and implementing measures within the various business units and processes. The comprehensive optimisation of risk management throughout the company must also be addressed. In the context of IT, this means a comprehensive IT risk management process that is seamlessly integrated into the organisation's enterprise risk management. What this means in concrete terms:
- Aligning risk management with the goals and objectives of the organisation. Also ensuring that RM will maximise the attainment of the organisation's objectives and results.
- Identifying the risks. Systematically identifying and listing all those risks that affect an organisation and that may have an impact on successfully achieving objectives and targets.
- Assessing the risks. Analysing the risks identified in terms of the likelihood that they will occur, and their potential impact. Comparing the risks against pre-defined risk acceptance criteria to establish priorities for responding to the risks.
- Deciding on the strategy for managing risk. Defining how risk is to be managed in accordance with the company’s risk appetite. Should a risk be accepted, avoided, reduced, spread or transferred on the basis of the evaluation?
- Controlling the risk. Monitoring identified and current risks against predefined risk indicators to spot any changes. This way, it can be ascertained whether or not the measures have been successful.
- Making sure there is appropriate communication of risk. Communicating risks and their outcomes to stakeholders in a comprehensible, transparent way to inform them and enable them to take decisions.
Compliance
The term compliance means adherence to legal, contractual and internal company regulations as part of corporate management. For IT, this principally means ensuring that information security, availability, data retention and data protection are safeguarded throughout the entire lifecycle. Compliance includes putting in place IT controls, as well as testing and observing them. What this can mean in concrete terms:
- Drawing up guidelines for compliance with internal and external regulations and commonly accepted practices (mission statement or code of conduct).
- Establishing methods of assessment for identifying skills and maturity levels.
- Defining indicators that can be used – preventative, proactive and reactive. Predicting the security situation via practice, process and risk assessments, and technical control data.
- Developing economic models to define a hierarchy of investments and quantify how efficient they are.
- Ensuring continuous monitoring and response.
Implementing GRC efficiently
Today, progressive digitalisation means that companies are more and more closely interconnected, so a single event may have far-reaching effects. This why having an integrated GRC approach is very important. It means that companies are able to anticipate, understand and manage their risks in a comprehensive way. It helps them appreciate the correlation of current risks with compliance requirements and other GRC elements, to identify potential impacts on the business, and make these available to senior management. Thus, companies are able to assess risks and opportunities more effectively, make evidence-based strategic decisions, and respond efficiently to changes within and without the company.
There are many benefits to having a well-planned GRC strategy, such as better decision making, targeted IT investments and less fragmentation between departments and divisions to reduce silos, etc.
Incidentally, the experience we have gained in this area shows us that the combination of sustained corporate management with requirement-oriented compliance and effective risk management, together with an additional internal control system that covers the strategic level all the way to the operational level, is only efficient when companies can count on the right software tool.
Governance, risk & compliance is in your hands
An application that covers governance, risk and compliance provides management, the CISO / ISO, the data owner and end-users with the information they need. The information is used to understand the risks, make decisions on the basis of risk, and reduce negative consequences.
At InfoGuard, we have been working very successfully in this area with our partner HiScout for a number of years. You hadn’t heard about this solution yet? The GRC Tool by HiScout is an integrated system for managing, documenting and tracking a range of GRC. The solution is used across organisations, thus making it possible to take a comprehensive, collaborative approach to the GRC environment. Authorised users are able to efficiently aggregate risk and compliance information from across the organisation and then transform it into viable business intelligence that assists with decision making. The HiScout GRC solution has features like advanced risk analysis and reporting in real-time, making it ideally suited to the GRC requirements of modern, complex, global companies.
Would you like to find out more about HiScout, or have you got any questions about GRC? Our experts will be happy to show you the advantages of our GRC solution in a one-to-one meeting.
Minimum standard for increasing ICT resilience to cyber risks
In 2018, the Swiss Federal Office for National Economic Supply (BWL) launched a minimum standard to increase ICT resilience. The ICT minimum standard is principally aimed at the operators of critical infrastructures, but it can also be applied to all companies. Our InfoGuard experts will be happy to assist you.
In one of the next blog posts, you can find out about how to implement the ICT minimum standard efficiently and the added value for your company that results from it.
Never miss out on a blog post again by subscribing to our updates now:
Graphic source: https://de.wikipedia.org/wiki/Datei:GRC_forschungsrahmen.PNG






