The world of cyber security is growing ever more complex and changes are quicker than before – and its market grows accordingly. Countless solutions promise THE final protection against cyber risks. Is it possible, in such a flood, to find who is really ahead of everybody else? To answer this question, the US-based market research enterprise Gartner Inc. has been publishing for years its so-called "Magic Quadrant Reports", each focusing on one specific aspect of cyber security. This post shows you how it works, and – most important – how you can benefit from it.
Use some (cyber) magic
The Magic Quadrant is based on a research method that is meant to help restrict the choice of a possible provider and find direction.
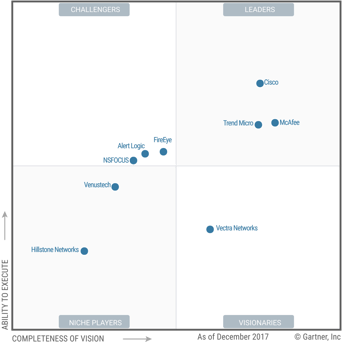 A visualisation tool is used to display the position of different vendors in a specific marketplace. The two-dimensional matrix places a different class of businesses in each quadrant. From bottom left, clockwise:
A visualisation tool is used to display the position of different vendors in a specific marketplace. The two-dimensional matrix places a different class of businesses in each quadrant. From bottom left, clockwise:
Niche Players are often relatively new in the marketplace. They do indeed offer a specific technology, but they are not (yet) capable of making full use of their strengths.
Challengers possess top-level skills and are usually fast growing businesses. But like with the Niche Players, their vision has room for growth.
Leaders can be found in the top right quadrant – the best position, as you will surely have guessed. They have a leading position in the marketplace and a clear vision. Their solution skills give them a strong influence on the development of the market.
Visionaires have a full, well-targeted vision, which makes them the leaders of tomorrow.
It's a simple and useful principle. However, Gartner Reports are useful not just for adopters of each individual technologies, but also for the vendors themselves. The Report is an independent source, which lets the vendor have an impartial view on his own strengths and weaknesses, those of his competitors, and also on his own potential for optimisation; in turn, competition is also made stronger. As a client, your business has the additional advantage of looking forward to better, more innovative solutions ahead in the future.
Gartner has pointed out Vectra as the only Visionary. Here are 3 reasons why
In its latest report, Gartner has placed our partner Vectra Networks as the only visionary for IDPS (Intrusion Detection & Prevention Systems). Let us see why. IDPS make use of additional methods such as Advanced Analytics, which help them find out threats that made their way across other security barriers. The approach used by Vectra is more innovative, in that it targets today's key themes in security operations. Gartner has judged Vectra a visionary in the field of Intrusion Detection and Prevention, for the following reasons:
- Developing IDS to make use of advanced analysis procedures such as machine learning is well-suited for the different methods of telemetry that this new technology makes available. This allows for new methods for detecting malevolent, undesired behaviours within the systems.
- The adoption of the TAP architecture (virtual Test Access Point), and the integration with hypervisors such as VMware, lets users integrate Vectra solutions without problems even in strongly virtualised environments such as public, private or hybrid cloud.
- The need for administrative resources for this product, compared to many other products, is minimal.
It is time to give priority to the discovery of attacks
The approach chosen by Vectra shows its differences from other vendors right from the development: they have clearly understood that, in order to detect cyber threats, the behaviour of attackers must be understood in depth. The latest, craftiest attackers do not limit themselves to just malware or exploits in their attacks; they use the same tools as system administrators, which of course make the detection much harder.
Infrastructures are growing more and more complex, and offer an ever-increasing attack surface. New systems for the detection of attacks must be simpler than traditional IDS, which require many sensors and must be constantly supervised. In addition, the search for threats must not be limited to the perimeter. The discovery technology must be anchored deep into the network if even the smallest sign of a cyber attack must be identified – for instance, internal reconnaissance, or lateral movement.
One thing that makes for some degree of the problem, is the background noise of the enormous mass of data. To be sure that the signs of an attack do not disappear, a specific method has been put in place to filter and limit the information flood, and to order risks by priority. This is the only way to guarantee that security analysts can react without delay precisely to those threats which make for the greatest risks.
Cognito™, Vectra's platform for the automated recognition and response to threats, bases its capabilities of discovering the fundamental behaviours, which are at the center of cyber attacks, on the direct analysis of network traffic. By combining data science, machine learning and behaviour analysis, Cognito can find out how an attacker actually proceeds. A central aspect of this structure is the fact that the system does not rely on traditional malware signatures or reputation lists; Cognito makes use of analytic procedures to track down unwanted anomalies, regardless of application – or indeed encryption. This brings out into full view those steps that are the point of strength of an attack, without which the attacker cannot reach his target.
To read more on the subject, download now the free Gartner Magic Quadrant Report 2018 for IDPS!
PS: If you want to know more about IDPS, cyber defence in general, and cyber security, subscribe now to our Blog Update! You will never miss any new issue, and you will benefit from the experience of our cyber security specialists.




