Digitalisation is affecting every area of the economy and society – in the more obvious areas of daily life as well as less visible areas such as OT. Here, safety and cyber security are elementary. After all, cyber attacks are now one of the biggest threats. It is a challenge for companies to ensure security in OT environments. In this blog post, you will learn how this security can be achieved.
Security in the physical OT world is different from virtual IT security
Industrial production is becoming increasingly digitised. New IT technology is finding its way into plants, autonomous, self-learning robots are manufacturing complex products, and self-driving vehicles are delivering components to the production lines. Two worlds are colliding – automation (OT) on the one hand and information technology (IT) on the other. New security risks are emerging with (I)IoT and Industry 4.0, because technical systems that were not previously connected to the internet are now also vulnerable to attack. Intentional or unintentional malfunctions can cause irreversible damage in the physical world, and unlike in the IT world, these cannot be resolved just with a patch.
Therefore, the vision is one of extensive connectivity and the utilisation of the resulting potential for synergy – be it in the entire network, or just related to the production systems of a company. By contrast, the reality is the merging of two complex worlds with equally complex and partially outdated or faulty interfaces. IT traditionally focuses on confidentiality, information security and data protection, whereas OT focuses on machine and system availability and the protection of employees and the environment. In German, we try to cover both areas with the word “Sicherheit” (security), whereas in English, two terms are used: Safety and Security. Safety tends to refer to operational safety, i.e. protecting people and the environment. Security, on the other hand, means protecting data and maintaining proper data processing.
Ensuring safety is not only necessary due to use in critical environments such as power plants, power supply or machine control, but also mandatory from a legal perspective (product liability, warranty, mandatory safety tests and certifications, etc.). Hence, numerous standards enforce a high level of protection, as the effects of a malfunction, e.g. due to a failure or a cyber-attack, can be extremely dangerous.
Once safety measures have been established, they usually retain their effectiveness over a longer period of time. This is also due to long product lifespans and less frequent updates. On the other hand, fast-moving IT security requires a completely different approach to updates and product renewals. In IT, improvements need to be made more frequently and more quickly, and this leads to more frequent updates but can also lead to IT products that are less mature being launched on the market. What's more, safety has been an issue for much longer than security, as the latter has only come into focus with increased digital networking – which means that there is also a greater body of experience and sufficient legal certainty and regulations to protect consumers in terms of safety.
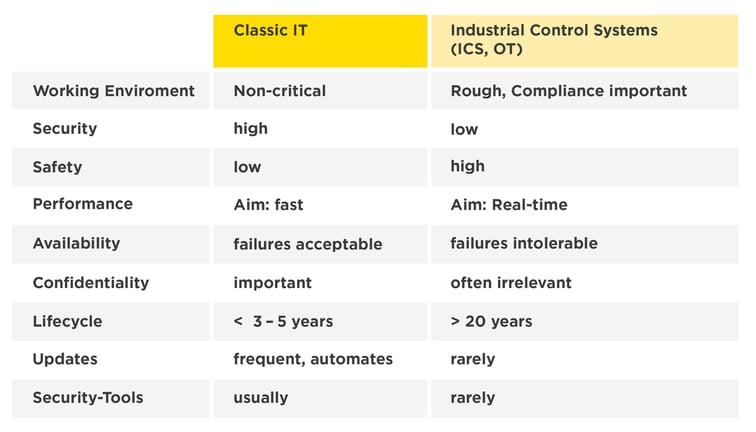
Differences between classic IT and OT
The table below shows the difference between these two worlds:
Considering the original separation of the two worlds (no OT-IT connection or only isolated communication and manual interfaces), it is unsurprising that after the establishment of product tests, consumer protection mechanisms, etc., OT has made quite a few headlines in terms of safety, but absolutely no headlines in the area of security for many years. (Unfortunately), the focus is clearly on “made” because with the increasing spread of IoT and the increasing digitalisation of the control of physical systems due to complex IT systems and networks, the two worlds are becoming more and more intertwined thus becoming targets for hackers. This is why it is important to recognise that “security” can be related to a variety of contexts, but that there is also an increasingly large intersection between the two areas. However, there are different approaches to problems identified in the two worlds, and understanding of the other side's issues is still rather low. Neither side (including the “general purpose” networks based on internet technology) seems particularly well prepared to manage shared end-to-end services using complex interfaces and protocols.
The danger of cyber-attacks is different for OT
For industrial systems, the hazard potential is structured in a completely different way than with classic IT. The failure of machines and systems (e.g. in the event of a power failure) can cause considerable damage. Here, milliseconds are often all it takes. The failure or malfunctioning of systems can also put people at risk, even cause irreversible damage.
The increasing digitalisation and the implementation of Industry 4.0 mean more and more often, safety and security are being placed in the same context. Components, systems and equipment are networked and digitally controlled, and the term industrial IT security is cropping up more and more often. Errors in security can become a safety problem and thereby impact people and the environment. If cyber criminals manage to penetrate the company network using infected emails, they can take over individual machines or entire production lines, bringing them to a standstill or manipulating certain sub-processes. This was also demonstrated by the cyber-attack carried out on the USA's biggest pipeline. At the time, around 50 million consumers were affected when the supply of petrol, diesel fuel and heating oil (around 2.5 million barrels per day) was compromised, and this also had a massive effect on crude oil and petrol prices. Furthermore, under certain circumstances, delivering manufactured products that are defective can ruin companies, and liabilities and claims for damages can also ruin the plant manufacturer.
The potential for danger in the production environment has increased even more with the use of CPS (Cyber Physical Systems), and attacks on SCADA systems have almost become part of everyday life. The growing networking of individual machines and plants creates a new transparency and brings many advantages, but in the harsh real-time world, there is an increasing risk of attacks, but in the harsh real-time world of production, established mechanisms for defending against cyber attacks are only partially effective.
Unfortunately, that is not all. There are many examples of outdated systems, interfaces and protocols in the production environment, with the associated issues of security, maintenance and operational monitoring. This means that both the potential dangers and the range of protective measures that need to be taken are extremely diverse, and they can quickly become an excessive burden on highly specialised companies and specialists. Regardless of the age of the systems, classical approaches have only a very limited effect in such complex environments. In production, what prevails (as you have seen in the table) are real-time requirements – and not only for communication. The systems must also be available round the clock (24/7). This means that no servicing time is available to perform updates.
However, security is not improved simply by having a common context. This can only be achieved through close, responsible cooperation between the disciplines of safety and security. The increasingly practiced vertical integration requires comprehensive end-to-end approaches to ensure effective protection against cyber attacks on companies. Thus, the circle between IT and OT is closed here. In the same way that IT is unable to tackle production-related challenges, OT is unable to tackle security requirements on its own.
OT security to ensure that safety remains guaranteed
Therefore, both areas, IT and OT, must work hand in hand, and this imperative to work together is becoming stronger and stronger as digitalisation increases. Consumers as well as regulators and legislators are demanding a secure end-to-end chain, and justifiably they do not make a distinction where errors that lead to insecure products or services occur. This does not only apply to the issue of cyber security. Clear guidelines apply to safety and extensive assessments have to be carried out, but in many cases, OT security is still severely neglected. With OT and IoT integrations, production environments are evolving into a networked world, and this is where cyber security is crucial, alongside established product and production security.
To fend off attacks, companies should be thinking about the security of new machines or systems in their own operational and IT context before developing or integrating them, and clarify these aspects in advance with the operator. Here, security differs significantly from the classic IT environment: With lifetimes averaging 20 years and more, updating firmware, operating systems and APIs as well as the deployment of security measures become significantly more difficult, and that’s assuming that the appropriate support is even available from the manufacturer over such long periods of time and that the systems have not been certified in such a way that updates lead to costly re-certification. Where a custom solution is implemented that is specially adapted to the customer's needs, it is often not compatible with standardised IT security systems. The IEC 62443 standard has now established itself as an internationally recognised standard for security in the environment of the process and automation industry – we have already described this in detail in another article.
Transparency in OT- and ICS environments is fundamental
With the digitalisation of industrial plants, the requirements for OT security have increased significantly, and now OT measures need to be adapted to meet these demands. This requires technologies, for example those of our partner Nozomi Networks, for the continuous monitoring of industrial control and automation systems. With their support, it is possible to reliably implement fully digitalised, networked industrial production beyond the limits of today's manufacturing processes. Here, an important role is played by the production-oriented recording of communications between systems and machines, then analysing it in real time for safety threats. Nozomi makes it possible to counter growing cyber risks through network transparency, threat detection and insight into operational processes. This creates the level of security required for Industry 4.0 production processes and business models without the costly conversion of existing systems. Would you like to find out more? Contact us – we will be pleased to present the Nozomi Networks solution to you in a one-to-one meeting. In addition to this, it is essential for security, the protection of intellectual property and corresponding market advantages, as well as for sustainable risk management, that at all times a company has a sufficiently precise knowledge of its critical assets requiring protection and what their condition is. These include, for example, plant and machinery, production processes and procedures, data on manufacturing parameters, formulations and process expertise. These critical assets requiring protection must be properly documented and regularly updated. The aim is to show the potential threats and interrelationships for the individual assets. The criticality, the need for protection and the measures to be taken are derived based on the probability of their occurrence and the potential extent of the damage. The higher the risk rating is for an asset, the greater the scrutiny of every access to or via that asset.
In addition to this, it is essential for security, the protection of intellectual property and corresponding market advantages, as well as for sustainable risk management, that at all times a company has a sufficiently precise knowledge of its critical assets requiring protection and what their condition is. These include, for example, plant and machinery, production processes and procedures, data on manufacturing parameters, formulations and process expertise. These critical assets requiring protection must be properly documented and regularly updated. The aim is to show the potential threats and interrelationships for the individual assets. The criticality, the need for protection and the measures to be taken are derived based on the probability of their occurrence and the potential extent of the damage. The higher the risk rating is for an asset, the greater the scrutiny of every access to or via that asset.
Alongside technical measures, companies should also develop and implement the security guidelines and processes required to control and optimise the technical protection measures. As part of this, roles, responsibilities and accountabilities must also be defined within the IT and OT world, as well as across departments. In addition, companies should conduct regular incident response exercises to test organisational effectiveness. This is the only way to guarantee safety and security against the background of complex IT-OT environments and a constantly rising number of attackers.




