InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
A look into the cyber crystal ball – the Threat Report 2020

The rapid developments in the world of cyber security are nothing new. And although – or because – you have to be prepared for everything all the time, it's a good idea to take a look into the future, isn’t it? Our partner, Sophos, is an expert in artificial intelligence endpoint protection but it cannot predict the future. However, research conducted over the past 12 months has enabled its specialists to identify trends and at least give an idea of what threats we will be facing in 2020. First of all, the general conclusion is that threats will not only be rapidly growing in terms of quality and quantity but will also become increasingly unpredictable. You can find out in this blog post what threat report topics you can get ready for.
Automated ransomware attacks
Ransomware is still on the increase (remember CryptoLocker and WannaCry). According to the Global Ransomware Report, in 2019 (to date) 85 per cent of IT service providers have reported being affected by ransomware. In 2018 the figure was "only" 79 per cent, with the growth accelerating. What is the Sophos Threat Report forecasting for 2020?
Of course, it is not possible to predict the exact numbers. However, the Threat Report warns about automated active attacks. These can manipulate tools so that they work against you. Obviously, security controls are bypassed. Against this background, an increasingly popular method among hackers is to capture and misuse credentials from remote monitoring and management (RMM) solutions. RMM makes it possible to remotely manage IT infrastructures, which is why managed service providers prefer to use it. The issue, however, is that wide-ranging rights are involved, and these offer just as great a potential for damage in the event of abuse.
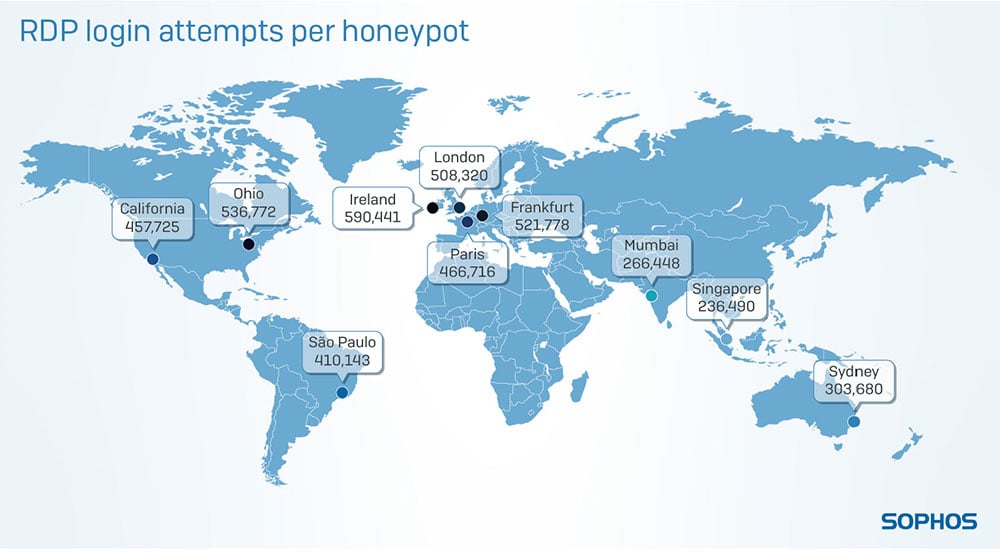 Sophos launched an experiment and set up honeypots around the world. The result was almost 600,000 brute force login attempts. (Image source: Sophos)
Sophos launched an experiment and set up honeypots around the world. The result was almost 600,000 brute force login attempts. (Image source: Sophos)
Infected malware apps
Cyber criminals have long since identified the "potential" of mobile devices as a target for attack, so it is hardly surprising that cyber criminals are increasingly targeting mobile apps. Since 2019, what are known as fleeceware apps that misuse subscriptions and aggressive adware have become widespread. These and other apps, including browser plug-ins, will spread more malware in the future. In the threat report, Sophos cites Hiddad malware (adware) as an example. This hides on the device and remains undetected for as long as possible. The trick is that even if the app icon has disappeared, the malware stubbornly remains in the background, so it is hard to locate and delete it.
Machine learning as a risk for your own cyber security
Everyone is talking about machine learning. Many people are lauding its benefits for cyber security – some even see it as "the best" solution in the fight against cyber criminals, but machine learning can also have the opposite effect and turn into a disaster. For example, the Threat Report describes how machine learning-based security systems can be tricked.
Machine learning learns through a constant flow of new data. If a cyber criminal were to send wrong data and in doing so influences the algorithm, a system could be bypassed. Although of course, machine learning also offers further potential for supporting cyber security and cyber defence, for example recognising text messages and URLs in potential phishing mails. As the saying goes, “there are two sides to every coin”.
Cloud security – little mistakes, major damage
Cloud computing has revolutionised IT in so many ways and offers tangible business benefits too, but clouds are complex and many errors can creep in, including with release management. Sensitive information of this kind is, of course, a real source of nourishment for cyber criminals.
 Configuration errors are one of the greatest security risks for cloud computing, so it's advisable to have them checked for weak points, for example by a targeted penetration test. You can find out about the exact procedures carried out by our experts in a cloud penetration test, and read more information about cloud security in previous cyber security blog posts.
Configuration errors are one of the greatest security risks for cloud computing, so it's advisable to have them checked for weak points, for example by a targeted penetration test. You can find out about the exact procedures carried out by our experts in a cloud penetration test, and read more information about cloud security in previous cyber security blog posts.
By the way, are you an Office 365 user? This cloud solution is becoming more popular than ever. However, often the risks are ignored and most people don't even know about them. Our free checklist tells you what they are and what measures are recommended by our cyber security experts to simply optimize O365 security. Download it now! (Only in German available.)
Cyber security as a factor in success
Of course, the Sophos Threat Report mentions other risks as well. Unnoticed attacks on Internet-connected devices or remote desktop protocol (RDP), a popular entry point for cyber criminals, are just two of them. The gist of the report is clear even without needing to explain all the details: Cyber security will become one of the most important success factors for staying competitive in the future - for every company! This is why it's better to take the appropriate action today than tomorrow and call in cyber security experts like InfoGuard. How can we help you? Contact us!
Blog

NIS2, CRA, KRITIS und der 6. März: Jetzt zählt die nachweisbare Umsetzung!

ISMS nach ISO 27001 schnell implementieren? Ein Realitätscheck.



