InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Efficiently Implementing and maintaining the ICT minimum standard

It is hard to supply vital goods and services in Switzerland without well-functioning information and communication technology (ICT). However, there is a growing threat coming from process risks as well as cyber risks. The Swiss Federal Office for National Economic Supply (BWL) has reacted to this and has developed a minimum standard for ICT based on the NIST CSF (Cyber Security Framework). The ICT minimum standard is primarily aimed at the operators of critical infrastructures, but in principle, it can be applied to any organisation. You can read in this blog post exactly why you should apply it to yours.
There is a certain risk inherent in any ICT system. However, this can be reduced to an acceptable level by taking the appropriate measures. In an earlier article, we already explained how important the issue of Governance, Risk & Compliance (GRC) is for a company. This is all the more important when it comes to protecting critical infrastructures. For this reason, in 2018 the Federal Office for National Economic Supply (BWL) launched the ICT minimum standard, to protect and safeguard the confidentiality, integrity and availability of ICT systems in critical infrastructures.
The basis for the ICT minimum standard consists of a risk analysis on cyber risks. The minimum standard for making information and communication technology (ICT) stronger and more resilient is based on the internationally recognised NIST Cyber Security Framework (NIST CSF), and this is completed by other industry standards, such as the NIST Guide to Industrial Control Systems (ICS), ISO 2700x, COBIT or the BSI. The ICT minimum standard should not be seen as competing with existing standards. It is compatible with them but it has a deliberately reduced scope. This is intended to make it easier to enter into the subject while still ensuring a high level of protection.
ICT security strategy – defence in depth
The ICT security strategy needs to be geared towards protecting the critical ICT assets required for business processes. This requires a multi-layered approach, known as “defence in depth”, which operates on the principle that it is more difficult for an attacker to break through a complex, multi-layered defence system than a single barrier. Thus, the aim of the holistic concept of defence in depth is to identify and respond to ICT security breaches, then to minimise the consequences arising from the security breach. Resources should be deployed to ensure effective protection against known risks and the comprehensive monitoring of potential future risks.
The 106 measures of the ICT minimum standard call for assistance
The ICT minimum standard contains over 100 precise, practical instructions for improving ICT resilience. The proposed measures are both organisational and technical. They include guidelines for activities such as drawing up a complete inventory of hardware and software, employee training and courses, data protection guidelines and measures for the early detection of threats, to name but a few. The standard’s risk-based approach makes it possible to implement different levels of protection which are tailored to the needs of the organisation. It is a major challenge to stay in control of all this and to remain in a position to provide information to stakeholders at any given time.
What you need to consider when implementing the ICT minimum standard
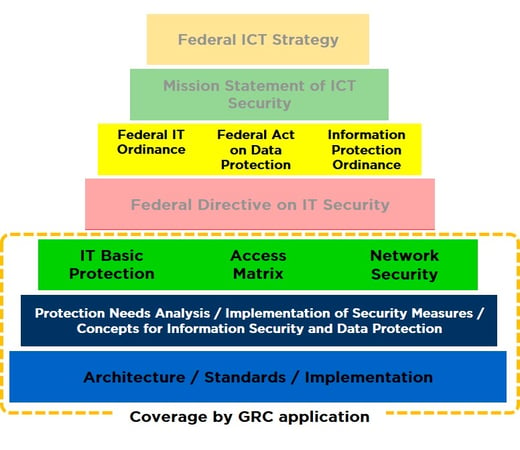
In your role as the IT Security Officer or CISO in a federal or government-related environment, you are faced with the difficult task of implementing the federal ordinances and directives relating to information security, and regularly reviewing and updating them. It is compulsory for the relevant security documents, such as the protection requirements analysis (Schuban, P041) or the information security and data protection concept (ISDS, P042) for the corresponding ICT protection assets of the administrative unit, to be drawn up on time. This also includes compliance with the requirements of the ICT basic protection and periodically revising and adapting them.
In general, security processes are difficult or impossible to implement when done using a decentralised approach. Also, there is a lack of consolidated information (situation picture) or risk presentation for the entire administrative or organisational unit. The following questions are just some of those that you will almost certainly be faced with at some point when you implement the ICT minimum standard:
- Do the (target) systems meet all the relevant requirements of the ICT minimum standard and ISDS?
- Do the components meet all requirements and do they meet the specifications?
- Are all the relevant requirements of the ICT minimum standard and ISDS met?
- What divergences from an increased need for protection still exist?
- What is the status as regards the implementation of measures?
You can only reliably answer the questions above and other questions related to the security situation picture by actively managing your ISDS concepts, risk assessments and the ICT minimum standard.
The basis for defining information security and data protection measures is the ISDS concept with its risk analysis. It shows the existing residual risks that arise from operating the ICT systems and that are linked to the organisation.
Always keep everything under control with an ICT application
The challenges of identifying risks, prioritising the need for action, tracking measures, etc. can only be overcome in the long term with support from workflow-based processes (in specialised applications). Companies should, therefore, consider using an ICT platform that both assists with and ensures the monitoring, measurement and control of the requirements arising from the ICT minimum standard and the resulting risks and ISDS concepts, centrally and on an IT or workflow basis.
An ICT platform assists security officers in building a company-wide, risk-aware culture and in promoting best practice in terms of cyber security. It also supports them in standardising policies, procedures, reports and analysis of impacts on the business, including standardising IT risk management reports that include all facets of risk management company-wide. However, a platform like this also makes it possible for the supply chain manager and the entire management of the company to make cyber security information accessible in a way that can be easily understood. This should create awareness of the existing and potential threats arising from business activity, growth and digital transformation.
What is the ideal ICT solution? Our favourite one!
The ICT application which we have adapted to meet Swiss specifications, working in an integrated collaboration with our partner HiScout, completely covers the requirements of the ICT minimum standard and also supports the HERMES project method. Analysis of protection requirements (P0041), ISDS concepts (P0042) and risk analysis can be centralised and produced in line with current processes. In the basic version, the ICT application is ready for use without the need for any adjustments. HiScout has already been used successfully by us to support the cyber security process in several companies and organisations.
Unnecessary manual work is eliminated due to integrated workflows, extended risk analysis and real-time reporting, thus continuously improving the maturity in the GRC disciplines. All stakeholders are also guaranteed to have access to the latest information.
What is your company's situation as regards GRC / ICT applications? If you would like to find out more about our HiScout solution, please contact us. Our Cyber Security consultants will be happy to advise you.
Graphic based on: https://www.isb.admin.ch/isb/de/home/ikt-vorgaben/sicherheit/si001-ikt-grundschutz_in_der_bundesverwaltung.html
Blog

NIS2, CRA, KRITIS, and March 6: Now it's Time to Show you're Doing it!

Want to implement ISMS according to ISO 27001 quickly? A reality check.


