InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Cyber Resilience Act – Get Yourself and Your Products up to Speed for the CRA

With the planned future increase in the cyber resilience of digital products, the preparations that hardware manufacturers, software developers, distributors and importers of digital products on the EU market are required to make are also set to intensify. With this in mind, the European Commission presented the draft Cyber Resilience Act (CRA for short) in September 2022. The CRA is designed to improve the cyber security of products that can be connected to each other or to the Internet. This article explains precisely what the CRA is and why the CRA has the potential to become one of the EU’s most important cyber security laws.
The Cyber Resilience Act (CRA) for products with digital elements strengthens cyber security regulations to ensure safer hardware and software products. The CRA and the binding cyber security requirements formulated within it aim to achieve goals including the following:
- Ensuring that products with digital elements placed on the EU market meet essential cyber security requirements and have fewer vulnerabilities.
- Manufacturers are and remain responsible for cyber security throughout a product’s life cycle.
- Improving transparency regarding the security of hardware and software products.
- Commercial users and consumers benefit from better protection.
The CRA applies to products that are: sold to end consumers, used in companies for production, sourced as precursors and further processed, or part of supply chains. The draft CRA envisages a number of measures to increase the cyber security of products.
The CRA is closely linked to other cyber security legislation such as the Network and Information Security Directive (NIS2), the Cyber Security Act, the Artificial Intelligence Act (AI Act) and the General Data Protection Regulation (GDPR, in particular the “data protection by design” and “cyber security” elements).
The Cyber Resilience Act is comprehensive – and demanding
In addition, the CRA sets out a number of essential requirements for hardware manufacturers, software developers, distributors and importers offering digital products or services on the EU market. The requirements of the CRA include:
- An “adequate” level of cyber security
- A ban on selling or placing on the market products with known security vulnerabilities
- Protection against unauthorised access
- Limiting the points of attack and minimising the impact of incidents
- Security through standard configuration (security-by-design)
- Minimising the points of attack
- Confidentiality of data through: a) encryption, b) protection of data integrity and c) data minimisation
Once the products are placed on the EU market, their manufacturers are subject to a duty of care for at least five years. The CRA covers a wide range of hardware and software. The same cyber security requirements apply to all products, but the type of conformity assessment is adapted to the respective risk level.
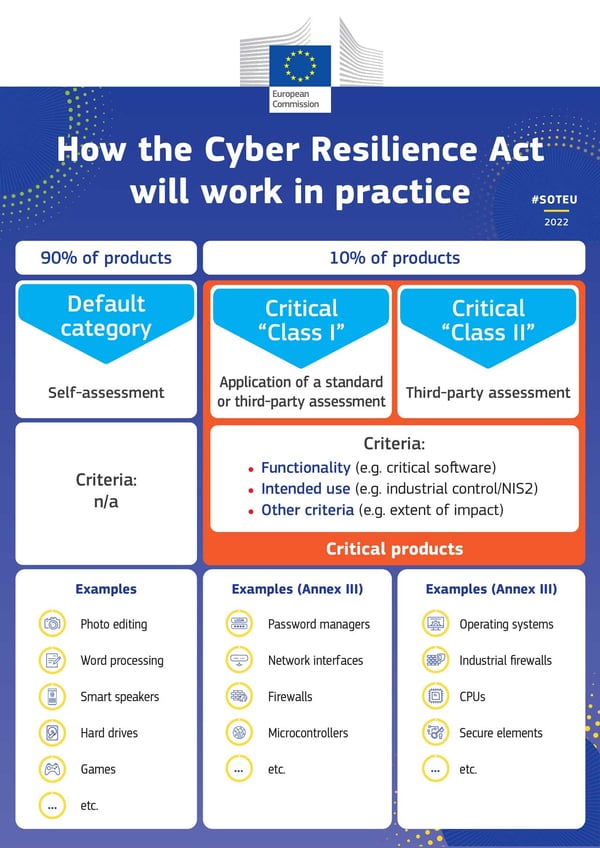
The CRA’s three-stage product categorisation
The CRA divides the products into three categories: class I; class II; not classified (standard category).
- The standard category consists of low-risk products covering 90% of the market (assumption), including smart toys, televisions or refrigerators. Products in this category would require companies to self-assess to ensure they meet cyber security standards.
The The two categories for critical products are:
- The first category (class I) includes browsers, password managers, anti-virus programs, firewalls, virtual private networks (VPNs), network management, systems, physical network interfaces, routers and chips used for equipment covered by the NIS2 Directive. It also includes all operating systems, microprocessors and industrial IoT devices that do not fall within class II.
- The second category (class 2) includes higher-risk products such as desktop and mobile devices, virtualised operating systems, digital certificate issuers, general purpose microprocessors, card readers, robotic sensors, smart meters and all IoT devices, routers and firewalls intended for industrial use.
Source: European Commission
The categories of class I and class II differ mainly in terms of the prescribed conformity process. Class I must involve the application of a standard or the performance of a third-party assessment to demonstrate compliance. Class II requires a mandatory third-party conformity assessment.
Products already covered by other EU regulations are excluded from the Cyber Resilience Act. These include motor vehicles, aviation systems and medical devices for human consumption, as well as software-as-a-service (SaaS) products covered by the NIS2 Directive. The European Commission is empowered to update and clarify the list of products covered by the Act.
Preparation is everything – including with the CRA
Steps that need to be taken to prepare for the Cyber Resilience Act include the following:
- Carefully monitoring the development of the CRA and preparing for the CRA now.
- Determining which category the products belong to: standard, class I or class II.
- Determining the lifecycle of the products as need be, ensure product monitoring throughout the lifecycle and provide the necessary security updates throughout the lifecycle.
- Security-by-design: security-by-design should become the standard.
- Security-by-default: products must be as secure as possible as delivered.
- IT security assessments: performing a cyber-security risk assessment to establish relevant risks and the underlying requirements that need to be met. IT security assessments need to be performed in each product production phase (planning, design, development, delivery and subsequent maintenance).
- Documentation of cyber security (in the technical documentation), vulnerabilities and third party components used for each product.
- Manufacturer’s warranty: manufacturers may only sell products without any known vulnerabilities.
- Event logging: security-relevant digital events in a device’s work process are recorded in the background.
- Existing products are monitored with regard to cyber security and vulnerabilities.
- Reporting of security vulnerabilities: capability to report and share potential security vulnerabilities.
- User information: users are informed about fixed vulnerabilities and cyber security incidents.
- Provision of information and recommendations for action with regard to the cyber security of the individual products.
- Incident reporting: manufacturers must report cyber security incidents and actively exploited vulnerabilities to the European Cyber Security Agency (ENISA) within 24 hours.
Although the points mentioned seem quite comprehensive, the CRA is still a work in progress. The European Parliament and the Council are currently reviewing the draft. As things stand, the CRA allows two years after its adoption for economic stakeholders and member states to adapt to the new requirements. The obligation to report actively exploited vulnerabilities and incidents will apply after one year.
Sanctions are modelled on the GDPR. In case of violations, the competent regulatory authorities can have products withdrawn from the market and impose fines of up to €15 million or 2.5 percent of the violating company’s global turnover (whichever is higher).
Not yet CRA-ready? InfoGuard will support you!
Are you also affected by the Cyber Resilience Act? If you are not yet ready: don’t worry. Our consulting specialists are available to provide you with expert advice and support, for example in the areas of NIST CSF, security assessments, architecture etc. Contact us for a no-obligation discussion and a quote. You can find out more about our Security Consulting Services here:
Blog

ISMS nach ISO 27001 schnell implementieren? Ein Realitätscheck.

OT Security: Wie Industrie und KRITIS ihre Cyberresilienz nach ISA/IEC 62443 sichern