InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Cyber Threat Intelligence Insights: Timing of Ransomware Incidents


Ransomware remains the biggest threat to most businesses, and these attacks consist of four general steps:
-
Initial Access: the attackers gain access to an organisation’s network.
-
Lateral Movement: attackers manually move from the Initial Access point to other points of interest on the network. These are usually servers that contain important data or personally identifiable information (PII), or a domain controller.
-
Exfiltration: the above mentioned data is copied from the victim’s network.
-
Encryption: ransomware is deployed.
The objective of this type of attack is to extort the victim in two main ways: First, through recovery of the data by decrypting it, and second, in preventing the stolen data from being published or sold.
Background to cybercrime
In recent years, ransomware has become a lucrative criminal activity favoured by numerous attackers. In 2022 alone, CSIRT dealt with at least eleven different ransomware families.
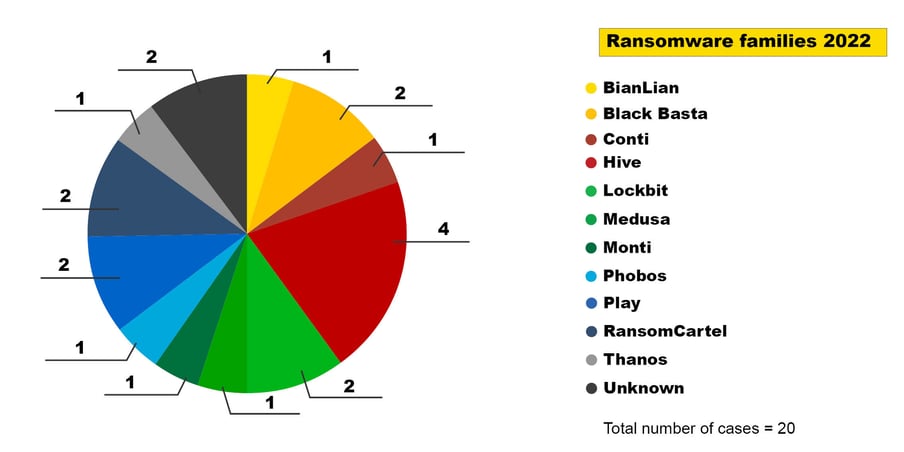
Figure 1: Ransomware families in 2022
While we tend to talk about an attack by this or that ransomware family, this is often an analytical shortcut: ransomware software is developed by a criminal entity that rents out its software, support for that software and often a platform for publishing the data. This market is known as Ransomware-as-a-Service (RaaS). While the ransom note, negotiation portal and release page all indicate a specific ransomware family, they provide no hints as to the actual attackers (affiliates/operators) carrying out the attack.
This Ransomware-as-a-Service (RaaS) offering appears to be a specialisation that has evolved in the Cybercrime-as-a-Service (CaaS) ecosystem. The reporting and analysis center for information security MELANI, the predecessor of NCSC.ch, described the development of ransomware in 2019 and the emergence of RaaS (see MELANI Semiannual Report 2019-1). In that context, the type of ransomware families that the InfoGuard CSIRT dealt with shows the growth and dynamics of the RaaS market.
Other types of operators are also active in the CaaS ecosystem. For this blog post, we are interested in those groups that seem to specialise in Initial Access. The main activities of these groups are maintaining and developing access to networks. Some of the more infamous groups are Dridex, Emotet, Bumblebee and Qakbot. Many of these malware families used to be banking Trojans before they specialised in reselling network access to third parties. However, we believe that there are other groups about which less is known because they do not rely on malware to gain access.
InfoGuard CSIRT ransomware cases
With a general idea of how the cybercrime ecosystem may be organised, let’s take a look at our dataset. It consists of the 20 ransomware cases that InfoGuard CSIRT dealt with in 2022.
Since we do not want to compare apples with oranges, the following points influence our data and thus the results should be taken into account:
-
The size and complexity of the victim’s network
-
The protective measures taken by the victim
-
The attackers’ resources and capabilities
Although this is only a small subset of the world’s cases, we have come across interesting patterns that we think could be valuable. Nevertheless, we welcome any data-based critique.
Low diversity in Initial Access
One of the first features we noticed was the fairly low diversity in Initial Access.
-
VPN/RDP access: Here, attackers gained access to the network with legitimate VPN or RDP credentials. We did not further distinguish how the attackers obtained the login credentials. However, examples include brute forcing, prior phishing or otherwise leaked credentials. In any case, legitimate credentials were used in all 13 cases.
-
Vulnerability: To gain access to the network, attackers exploited a known and internet exposed vulnerability not patched by the victim.
-
Malspam: Malware families such as Bumblebee, Dridex, Emotet and Qakbot were used for Initial Access. These were sent to the victim via a (mass) email. We did not distinguish whether the infection occurred via a malicious macro or some other method.
The most common form of Initial Access among ransomware cases in 2022 was VPN/RDP access, with 13 cases. In the remaining seven incidents, the attackers gained access to the victim’s network either via malspam or by exploiting a vulnerability.
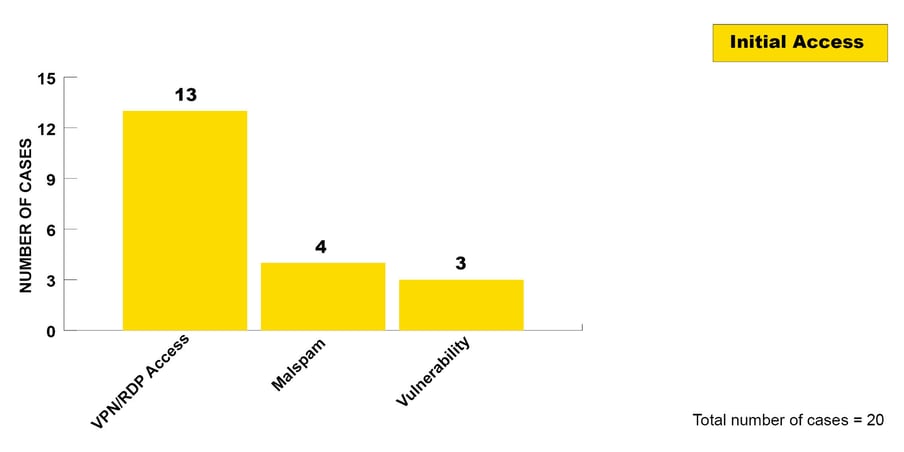
Figure 2: In all cases, one of these three Initial Access vectors was exploited.
A temporal pattern in ransomware attacks.
Thanks to the granularity of the data, we were able to consistently identify a pattern of time-based activity clusters.
After the Initial Access to the network by attackers, we often detected a pause in activity of varying lengths. Once attackers took further steps after the pause, the activities were “hands-on-keyboard” and ended in the encryption of the network or parts of it. This pattern is particularly clear in ransomware incidents, as such attacks from this point on involve noisy activity that an alert defender will quickly notice. This means that attackers usually aim to compromise the network quickly, rather than having an undetected presence, as is the case for example in espionage incidents.
This pattern – a pause after Initial Access followed by aggressive and noisy action – supports the hypothesis that a criminal ecosystem of providers, buyers and perpetrators has formed in the cyber domain: attackers can buy various tools, such as ransomware to execute an attack, on the darknet. Other actors, such as Initial Access brokers that specialise in breaking into networks and sell that access on illegal markets or confidential platforms. We believe that the pause between activity clusters can be explained by the triaging, the resale of an access and as well as the preparation for the next attack stage.
We divided the entire attack – from Initial Access, when attackers first set foot on the network, to the encryption – into two time intervals. To do this, we determined three points in time for each ransomware incident: The first point is on Initial Access, which marks the initial entry of an attacker into the victim’s network. The second point is Lateral Movement, which marks the point at which attackers begin to move or spread in the network with several successive steps with the ultimate aim – at the third point – of encrypting the systems in the network.
Note that we need an adapted definition of Lateral Movement in this analysis that differs from the standard one. In this case, Lateral Movement is defined as the start of a series of actions by the ransomware operator/perpetrator group as opposed to potential further movement after the Initial Access to the network by Initial Access brokers. This is usually clearly visible in the activity pattern:
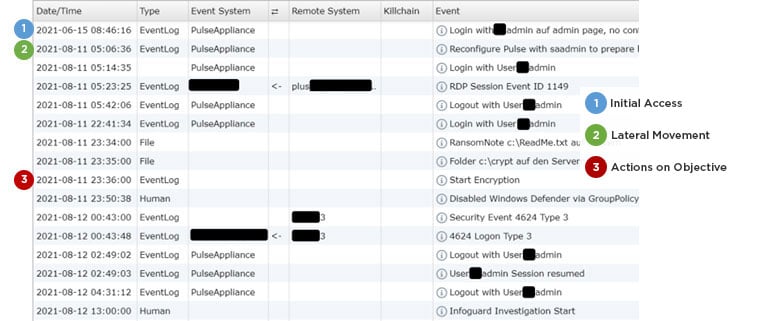
Figure 3: Documentation excerpt of an incident from the Aurora open source tool used by CSIRT during incidents.
In Figure 3, the time points and the activity clusters that emerged with them are visible. Point 1 is the point of Initial Access. Point 2 is the start of Lateral Movement with the goal of gaining access to valuable information and enabling the most comprehensive encryption possible. At point 3, the encryption is started by the attackers and is thus the point of “Actions on Objective”.
In this case, approximately 57 days elapse between points 1 and 2. During this period, attackers have access to the victim’s network, but no further activity by the attackers is visible. This is precisely the pattern of activity clusters that we have regularly observed in ransomware and we will now take a closer look at it in the following analysis.
Median time between Initial Access and Actions on Objective
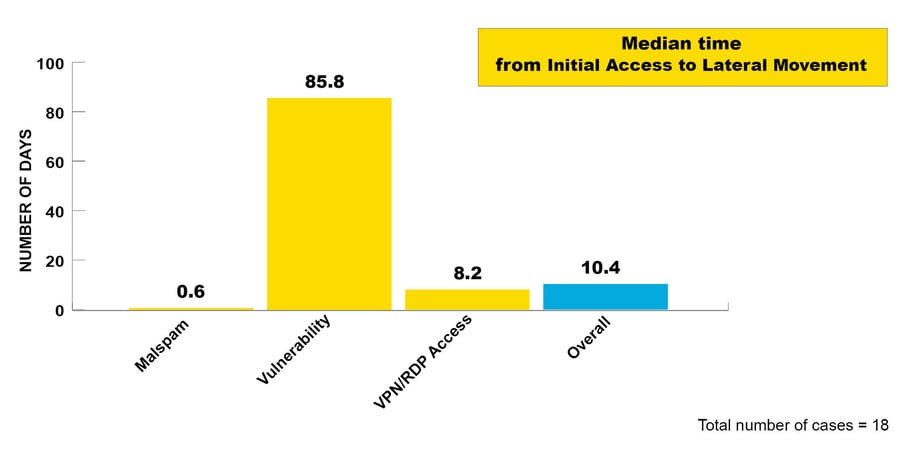
Figure 4: Median time from Initial Access to Lateral Movement
We see a crucial difference in temporality between the various methods of Initial Access, which is surprising at first glance. We have therefore made some assumptions that may explain the differences:
-
Malspam: In several cases, the malware has existed for a long time and used to be “just” Trojans and information stealers. One hypothesis is that attacker can quickly gather a trove of information about the victim’s identity in these cases. This may allow quicker price estimates and thus lead to a quicker sale of the illegal access.
-
Vulnerability: Cases in this category presented additional challenges. In some cases, the CSIRT was able to identify various attackers exploiting vulnerabilities. This makes it more difficult to identify which Initial Access might have been resold and eventually lead to a ransomware attack. The CSIRT additionally found cryptominers in some cases, which were used until the actual ransomware attack was launched. In these cases, a change in the payload was observed.
We assume that the attackers aim to compromise as many victims as possible and have automated the necessary operations. After the initial automated exploitation do the criminals start processing the information about the customer. It might therefore take more time to triage customers, gather additional information and ultimately sell access at a profitable price.
-
RDP/VPN access: As noted above, the CSIRT identified the use of legitimate credentials in these cases. One of our hypotheses is that the access is tested by the buyer or seller before the sale which would explain the first access, pause and then Lateral Movement.
The cybercriminal ecosystem is still new and hard to see. However, it is becoming increasingly clear that a division of labour has taken place.
Median time between Lateral Movement and Actions on Objective
Another factor we have studied is the time between Lateral Movement and Actions on Objective.
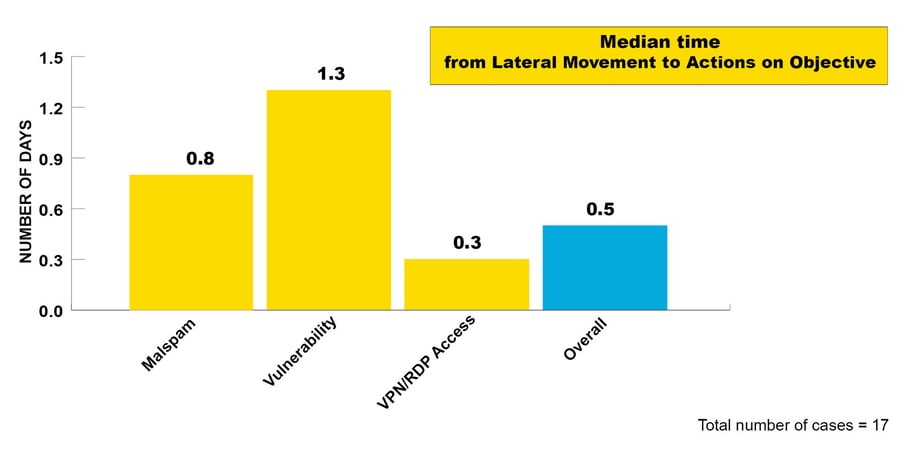
Figure 5: Median time from Lateral Movement to Actions on Objective
What is striking in comparison to the previous time interval is that the time between Lateral Movement and Actions on Objective is much shorter. Once an attacker has entered the network, they appear to work in relatively long shifts, depending on the complexity and defences of the network, with the ultimate aim of encrypting the network. Only in three of the 20 cases in 2022 was the incident noticed before encryption. In these three cases, the victims identified malicious behavior and contacted the CSIRT before a ransomware was deployed. The attacks in this stage could only be stopped with intensive effort by the CSIRT.
The data clearly shows that once ransomware operators are in the network, victims have significantly less time to detect and respond to the attack. It would be easier to remove the attacker from the network in the time interval between Initial Access and Lateral Movement. Antivirus solutions were in place that detected the attack in many cases. However, victims often did not have enough dedicated cyber security personnel to handle alerts on a regular basis, meaning that the attacker was not detected on the network.
Our takeaways
So what are the key points we can take away from this analysis? Using the CSIRT cases from last year, we gain additional understanding of the threat landscape, regional insight on cyber incidents and derive three important defensive measures:
-
MFA (multi-factor authentication) is strongly recommended and is essential on externally exposed services. This would have increased the cost for attackers in more than two-thirds of ransomware incidents.
-
Vulnerabilities should be patched as soon as possible and exposed services should be given priority.
-
Anti-virus alerts should be monitored and processed. A professional who has time and can raise the alert if necessary is important. In many cases, an external SOC service can be useful.
-
And if all else fails, the InfoGuard CSIRT 7x24 is at your service!
Learn more about our cyber defence services – from security operations and basic detection services to advanced detection and response services – on our website:
Blog

Preparing Swift CSCF v2026 Assessment: The Checklist for Independent Audits

Cyber security in the face of new risks: The 14th InfoGuard Innovation Day takes stock