InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Enhancing security through Cyber Threat Intelligence – a review of the CTI year


InfoGuard’s Cyber Threat Intelligence (CTI) team fulfils various tasks for its own protection and that of our customers. Of central importance: the identification of tendencies and trends of cyber attackers. In this article, we take a look back at the 53 largest cases handled by InfoGuard’s Computer Security Incident Response Team (CSIRT) last year with the aim of being even better prepared in 2023. With the aid of a threat landscape assessment, we can arrive at possible priorities and more optimal security investments.
Why a CTI annual review? And how?
An important part of our work as a Cyber Threat Intelligence (CTI) team is the continuous assessment of the threat landscape. This requires several steps. Given that our main goal is to improve IT security, we focus on threats from the cyber domain. However, we also pay attention to geopolitical factors that may influence the situation. Adopting this focus, we identify relevant data sources and process their content. From the resulting information, we compile a threat landscape assessment through analysis.
One of the most valuable sources of data are the traces of cyber attackers that the Computer Security Incident Response Team (CSIRT) continuously collects while handling incidents. For this article, we have deliberately focused on the 53 largest of all 158 cases handled by the CSIRT in 2022. These cases were significant because of their extent, effects and the existing traces of the perpetrators. This data was then processed to provide a detailed overview and evaluation of the attacks.
This review is not a complete assessment of the threat landscape. However, from the incidents analysed, generally applicable measures can be derived to increase protection from current cyber attacks.
Who are the victims of cyber attacks?
In order to classify the companies concerned in the cases analysed according to their economic activities, we used a sector list that can be found in the open source tool OpenCTI. This list fulfils our central requirement: its potential as a standard. A widespread use of a uniform list can enable a better overall perception of the threat landscape.
The list contains 22 different sectors, ten of which were involved in the 53 cases. From the 53 cases examined, 3 sectors also emerged that were most frequently affected. Even though the CSIRT was mostly active in the Finance, Manufacturing and Technology sectors, we do not want to generalise and conclude that the other sectors are less affected by cyber incidents. On the contrary, in our daily work it becomes clear time and again that any company can be affected – regardless of the sector and the size of the company.
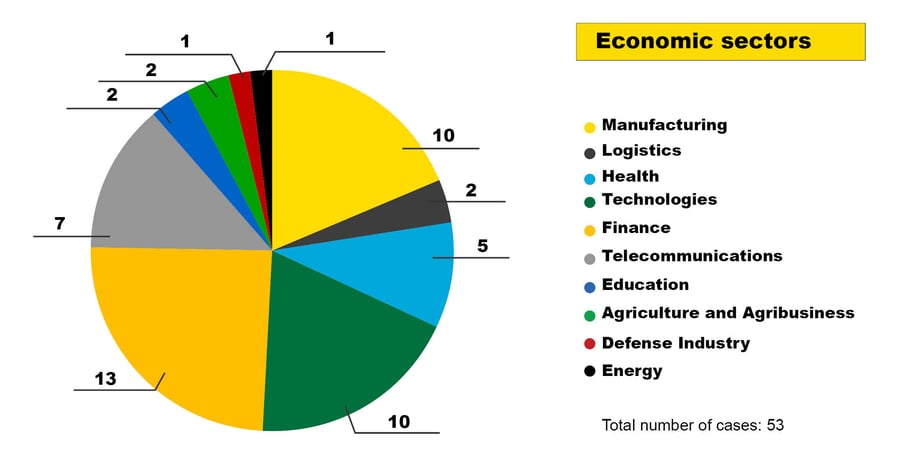
Figure 1: Economic sectors using OpenCTI’s listing of the 53 largest CSIRT cases in 2022
At the start, we briefly discussed our dataset, including the fact that we focused on the 53 largest cases. Several cases involving IT service providers also had an impact on this selection. Here, it became apparent that a large number of incidents can quickly stem from just one incident. The incidents spread to the customers of the IT service providers, who then also requested support from our CSIRT.
Preventive cyber security – IT service providers
This brings us to some initial preventive measures, as IT service providers have been the victims of cyber attacks with increasing frequency in recent years – and the trend is probably increasing.
In order to better protect yourself as a customer of an IT service provider against damage, we advise a contractual regulation. An important element: in the event of an incident, the IT service provider must inform the customer immediately so that no time is lost and measures can be initiated. In addition the IT service provider should at least apply the same security measures as to the customer. It should be noted that security measures never guarantee absolute security, but should reduce the risk.
The NCSC (National Cyber Security Centre) of Switzerland and the NCSC of the United Kingdom (UK) make further recommendations:
- NCSC CH: recommendations for cooperation with IT providers
- NCSC UK: using MSPs to administer your cloud services
How do cyber attackers gain initial access?
Before cyber attackers can cause damage, they must first gain access to the network, what is referred to as “initial access”. We have divided the different initial access methods of the 53 cases into eight categories.
- VPN/RDP access: Attackers gained access to the network through VPN or RDP credentials. We have not further differentiated how the attackers obtained the login credentials. However, attackers may have gained the access through brute forcing, previous phishing or credentials that have already been leaked. In any case, legitimate credentials were used in all 15 cases.
- Valid accounts: For initial access to exposed services and Office365, the attackers used legitimate credentials. Unlike the cases where legitimate VPN/RDP access was used, the attackers did not penetrate further into the corporate network.
- Vulnerability: To gain access to the network, attackers exploited a known vulnerability not patched by the victim.
- Malspam: Malware families such as Bumblebee, Dridex, Emotet and Qakbot were used for the initial access, which were sent to the victim via a (mass)email. We did not differentiate whether the infection was done via a malicious macro or another method.
- Phishing: In order for the attackers to get into a network, phishing emails were sent, resulting in a verifiable theft of credentials.
- Social engineering: Active social engineering was used to gain access to the network. The attackers gained the trust of the victims through a conversation, for example on social media. Then, they were convinced to open a malicious, individually delivered file.
- Zero-day exploit: The vulnerability that attackers exploited in this case was not yet known at the time of the attack.
- Insider threat: The attack was intentionally enabled by a (former) employee. Possible motivations are financial hardship, greed, blackmail or malicious intent.
Attackers most frequently used a VPN/RDP access (15 cases), other legitimate credentials under the valid accounts category (11 cases) or exploited vulnerabilities (11 cases) as initial access. These three vectors accounted for 70 % of successful initial accesses.
Preventive cyber security – priorities after initial access
In order to protect against cyber attacks, there are numerous measures that can increase the barriers for attackers. However, with the aid of a threat assessment, possible priorities can be derived in order to decide on more optimal security investments.
The following measures are recommended by our CSIRT based on this analysis. Had they been implemented, they would have been helped in disrupting the three most common initial access methods:
- MFA (multi-factor authentication): Setting up MFA can help prevent the following initial access methods: VPN/RDP access, phishing, valid accounts and social engineering. Priority should be given to exposed services. We assigned 34 of the 53 cases to these four categories.
- Minimise the attack surface: The second measure is not to expose services in the first place, unless absolutely necessary. This can reduce the attack surface and help against initial access via a vulnerability or via VPN/RDP access.
- Patch management: We strongly recommend setting up an efficient patch management system to quickly fix exposed services if needed.
In 85 % of the 53 cases examined, these measures could have helped to make it more difficult for the attackers to gain initial access to the network or prevented them from doing so.
Actions on Objective: What objective did cyber attackers pursue?
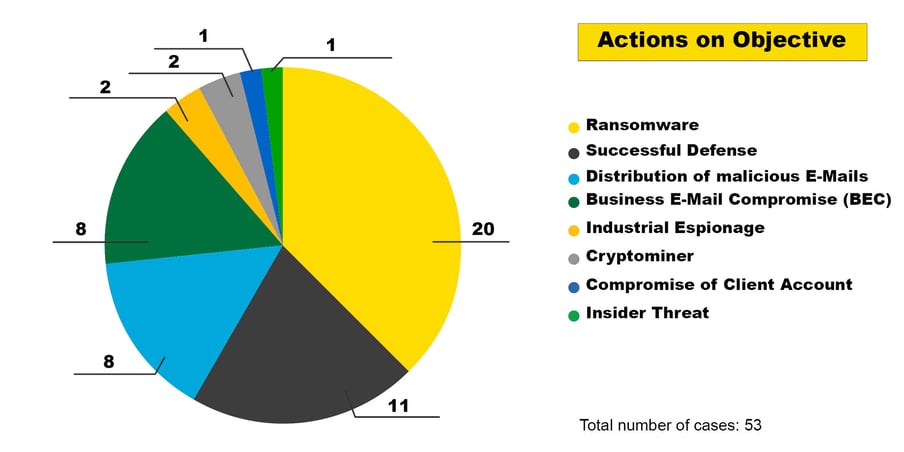
Figure 3: Actions on Objective of the 53 largest CSIRT cases in 2022
For the largest CSIRT cases last year, it is worth taking a look at the “Actions on Objective” according to the Cyber Kill Chain . We examined what the attackers were aiming for and what damage they caused.
- Ransomware: The goal of a ransomware attack is to blackmail the victims. To do this, attackers often use two means of pressure: firstly, the decryption of encrypted systems and data; secondly, the sale or publication of leaked data.
- Business Email Compromise (BEC): Employees are persuaded to execute transactions for the attackers by means of impersonating a false identity.
- Cryptominer: Attackers place cryptominers in the victim’s network.
- Industrial espionage: Attackers spy on the company with the aim of stealing intellectual property and company secrets.
- Insider threat: A current or former employee uses their special knowledge or access to harm the company.
- Distribution of malicious emails: Compromised email accounts are used to send phishing or malspam emails.
- Successful defence: Attackers are detected and stopped before greater damage can be done. The intentions of the attackers cannot be clearly determined.
- Customer account compromise: Attackers gain access to one or more accounts of a customer portal and use other people’s accounts to buy goods or make false payments.
Ransomware attacks remain the biggest threat
Ransomware attacks continue to pose the greatest threat, not least because of the high business impact. On the one hand, there is a risk of business interruption due to encrypted systems. In addition, we observed that data was often exfiltrated, which can lead to a data protection incident.
In a subsequent blog post, we will go into more detail about ransomware incidents. But there are already two questions that every company should be able to answer: first, how does the internal escalation process work in case of an incident? And secondly, who decides whether a system or the network can be disconnected from the internet in the event of an incident?
Our CTI review conclusion
The measures mentioned above are no guarantee that incidents can be prevented entirely. However, they increase the hurdle for attackers and give defenders more time to recognise and stop the attackers before Actions on Objective. This can minimise damage. In conclusion, let us once again summarise the recommended measures mentioned above:
-
IT service provider:
-
A contractual regulation – especially regarding immediate information in the event of a successful attack – is recommended.
-
At the very least, the same security standards should be in force at the IT service provider as at the customer.
-
-
MFA (multi-factor authentication) is recommended; on exposed services this is a must.
- Minimise the attack surface: do not expose services at all, unless absolutely necessary.
- Vulnerabilities must be patched immediately, if possible (patch management with priority on exposed services).
As you can see, our work is incredibly exciting and we want to support our customers and the public in protecting themselves against cyber attacks through our situation assessment.
If you don’t want to miss the next CTI blog post focusing on ransomware, all you have to do is to subscribe to our blog updates!
Blog

NIS2, CRA, KRITIS und der 6. März: Jetzt zählt die nachweisbare Umsetzung!

ISMS nach ISO 27001 schnell implementieren? Ein Realitätscheck.

