InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Fast, faster, XDR – how to speed up your detection & response!

Many security teams are unable to detect active attacks rapidly enough, so they fail to stop them in time. Despite the countless number of security tools, there is a lack of company-wide transparency and detailed analysis to reliably detect threats. Mutually isolated solutions generate loads of alerts and force your IT staff to constantly switch from one terminal to another. As a result, they often miss or fail to thoroughly analyse real attacks. In this blog post, we'll show you how to improve your Detect & Respond capabilities despite chronic time constraints and skills shortages.
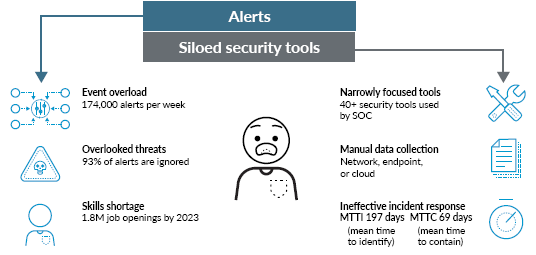
The threat landscape is rapidly changing. However, the biggest headache for many cybersecurity departments is not the endless number of risks, but the frustrating, repetitive tasks they have to perform every single day to reduce the interminable mountain of alerts their security tools have generated. Does this sound familiar to you too?
Analysts under attack
These days, security teams are faced with two massive challenges: a constant flood of attacks and an even greater number of alerts – an average of 174,000 alerts per week (according to “The State of SOAR Report”, 2018 by Demisto / Palo Alto Networks) – and this number has not gone down since then. To keep up with all these alerts, analysts often function in firefighting mode, trying to sort through as many alerts as possible every day. Unfortunately, these alerts often lack the context needed for an investigation, so analysts are forced to waste valuable time searching for more details. Consequently, over 90% of the alarms are ignored. This is clearly illustrated by the diagram below:
1, 2 or 3: Approaches to threat detection
Companies face two equally unappealing alternatives: they either exclusively rely on existing prevention products, or deploy a mishmash of disconnected detection and response products, so they are spoilt for choice:
- Businesses that rely on prevention tools for detection will most likely miss attacks such as highly evasive malware, malicious insiders and targeted attacks. This is because advanced attacks often do not include traditional “Indicators of Compromise” (IoC), such as attack signatures and malicious domains.
- The rising tide of attacks and the danger of missing attacks by using prevention tools has convinced companies to look at detection and response rather than focusing solely on defence, starting with SIEM, through NDR and EDR, to UEBA and SOAR. However, these tools also only provide a dedicated view of activity and require years of specialised experience to operate. Also, companies have to bear the cost of deploying and maintaining new network sensors and endpoint agents.
That’s why a new approach is urgently needed to solve today's cyber security challenges – one that simplifies every phase of security operations from threat detection to triage, investigation and response. You need three capabilities to help you reduce risk and at the same time, simplify operations:
- Threat prevention
As far as possible, prevention should automatically stop all threats in real-time or near real-time without manual review and for all your digital assets. - AI and machine learning
Your analysts should not have to manually analyse or correlate data to identify threats. Machine learning and analytics should do this by learning the unique characteristics of your business to detect anomalies. - Automation
To confirm attacks rapidly, analysts need alerts with extensive investigation details to enable action to be taken quickly.
These three functions, coordinated across all your critical resources, including network, endpoints and clouds, enable you to defend yourself against increasingly sophisticated threats and effectively protect your endpoints against attacks. This brings us to the third alternative!
Prevent, detect, investigate and defend against cyber threats –the magic word is XDR
Extended Detection and Response (XDR) products solve this problem by combining multiple security functions on a single platform for detecting and responding to security incidents. This enables you to have unified visibility across multiple attack vectors. Unlike SIEM systems which usually have a narrow compliance focus and act purely as a record-keeping system for security organisations, XDR focuses on the actual activity of threat detection and response. An XDR platform expands detection and response capabilities to identify threats that bypass preventive controls by using data from across the network, including the cloud and from all endpoints. This data is then enhanced using UEBA, a technique that can detect anomalies in behaviour across the network, machines, users and applications.
That's where the powerful Cortex XDR Agent from Palo Alto Networks comes in. It protects your endpoints from zero-day malware, file-less or script-based attacks and other hacking activities by analysing incoming files before and after execution. The agent is delivered from the cloud, so it provides your endpoints with immediate protection against complex threats, and it begins collecting security-related data immediately to improve detection and defence mechanisms. This harmonised data set is then used with orchestration and automation capabilities and versatile analytics to take immediate action before potential risks can cause any damage.
Cortex XDRTM – Extended Detection and Response from Palo Alto Networks
Cortex XDR is part of Cortex™, the cloud-based security solution from our partner Palo Alto Networks. For automated detection, investigation and defence against cyber threats The suite is based on the closely integrated products Cortex XDR and Cortex XSOAR, which facilitate the evolution of SOC processes from a primarily manual, reactive model with high resource requirements to an efficient, proactive, and automated mode of operation. This massively reduces the mean time taken to detect and defend against threats in each use case.
It is not just us saying this; the “MITRE ATT&CK cybersecurity evaluations” report says the same. Cortex XDR has achieved unrivalled detection results in real-world attack scenarios for two consecutive years.
XDR as a service from InfoGuard
And we've kept the best for last – you can get Cortex XDR from InfoGuard as a managed service, as a continuously staffed SOC (Security Operations Centre), which takes on functions like message management and searching for and defending against threats – from the network via endpoints to the cloud. In addition, we also depend on the XDR solutions from our partner Palo Alto Networks for our Cyber Defence Services.
Blog

Risiko Schatten-KI: In 4 Schritten zur sicheren KI-Nutzung nach ISO 42001

NIS2, CRA, KRITIS und der 6. März: Jetzt zählt die nachweisbare Umsetzung!


