InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Honeypots expose how insecure the internet is - and how SCION reduces the risk of attack

Cybercrime as a business case is more common in our everyday lives than you might think. We see it on a daily basis with our incident response practices. We’ve been analyzing the types and frequencies of attacks for our clients since 2017, and have seen an uptick in cybercrime incidents in Switzerland since 2020. Moreover, we noticed a pattern over the last two years; a startling increase in incidents resulting from network vulnerabilities. That’s why we decided to take a closer look: we devised a honeypot experiment comparing attack surface risk on three different networks. In this blog post, we have summarised the insights we have gained and what this means for you.
The Internet as the backbone of cybercrime
Our endeavor was to observe, analyze and draw some conclusions on the status of the Internet’s security today and to see just how different SCION is and what advantages it offers. SCION, developed at ETH Zurich, is a secure and reliable inter-domain routing protocol designed from its inception to enhance network control and transparency for communicating parties.
For this purpose, we partnered with Anapaya, the first and only commercial provider of SCION. Setting up the SCION honeypot was possible thanks to Anapaya’s EDGE and GATE solution.
Let’s start with the crux of the matter, in a powerful statement made by Ernesto Hartmann, our Chief Cyber Defence Officer:
“Through our incident response practices, we examined the business case of cybercrime. What we observed is that it is a social problem we are confronting. It's not only a challenge for enterprises but also for us as individuals. When we consider the potential of cybercrime, we recognize that, in terms of its scope, the potential customer base comprises half the world due to global Internet access. Thus, the Internet stands as the backbone of cybercrime.”
The status quo: how attackers get access to your infrastructure
Von Out of all the incidents we processed in 2022, 40% of them resulted from exploitable vulnerabilities in systems connected to the Internet. This was followed by multi-factor authentication (30%), phishing (27%) and supply chain (3%) attacks.
The three key trends linked to the vulnerability of systems connected to the Internet are:
- Ransomware evolution: Ransomware often moves from single to double extortion, where threat actors compromise data confidentiality in addition to system availability (to increase the likelihood of payout)
- Cloud compromises: The shift towards cloud technologies leads to an increase in cloud compromises, including fraud cases and business email compromise (BEC) incidents. For example, 5 million transactions went to the wrong IBAN number following a penetration into the system. This is a recurring type of attack.
- Zero-day vulnerabilities: zero-day exploits are also getting trickier, as hackers essentially have a backlog of opportunities built on such exploits; even if you find the weak spot in your network and patch it, they might have already been there, and it is just a matter of time till they use it.
What all three of these trends show us is that software vulnerabilities, which include system, application and network vulnerabilities, are the preferred entry point for threat actors. As Mathias Fuchs, our VP Investigations & Intelligence, puts it:
“Most criminal actors are opportunists, vultures. And the Internet today is full of opportunities. What we have to look at now is that the risk of attack is getting bigger and we are running out of time. The attacks are becoming more sophisticated and automated than ever before. This requires a clear and decisive response: it’s time to protect your edge services. Upgrading the Internet is a good way to reduce the likelihood of a successful attack.”
The proof is in the honeypot: measuring attack surface on today’s Internet vs SCION
In our honeypot experiment, we wanted to visualize the variation in attack surface risk between the Internet and SCION. A honeypot is a network-attached system set up to attract and lure potential attackers by mimicking the characteristics of a real system or network.
The question: How much does the attack surface available to malicious actors change with respect to the network that you are connecting to?
The setup: one honeypot in the Azure cloud, one in a Swiss residential network, and one on SCION with Anapaya EDGE and reachable only through Anapaya GATE.
Services exposed: Each honeypot runs a Secure Shell Protocol (SSH), a cryptographic network protocol for operating network services securely over an unsecured network and a telnet service, a service that is commonly exploited in attacks.
Honeypot data, explained:
These honeypots perfectly capture the kind of crime that is going on across the Internet right now. The timeframe we are looking at is November - December 2023.
The answer to how much attack surface changes depending on network: A lot! In fact, much more than we anticipated. The attack surface on SCION is up to 40,000 times less compared to Azure and 10,000 times less compared to the Swiss network in the timeframe measured.
- In total, there were just 3 intrusion attempts on the SCION honeypot, while ca. 121,000 on the Azure and 30,000 on the Swiss honeypot.
- We can safely infer that the SCION network probably faced intrusion attacks by actors operating from within Switzerland.
- This donut chart shows the split between the three honeypots and overall intrusion attempts:
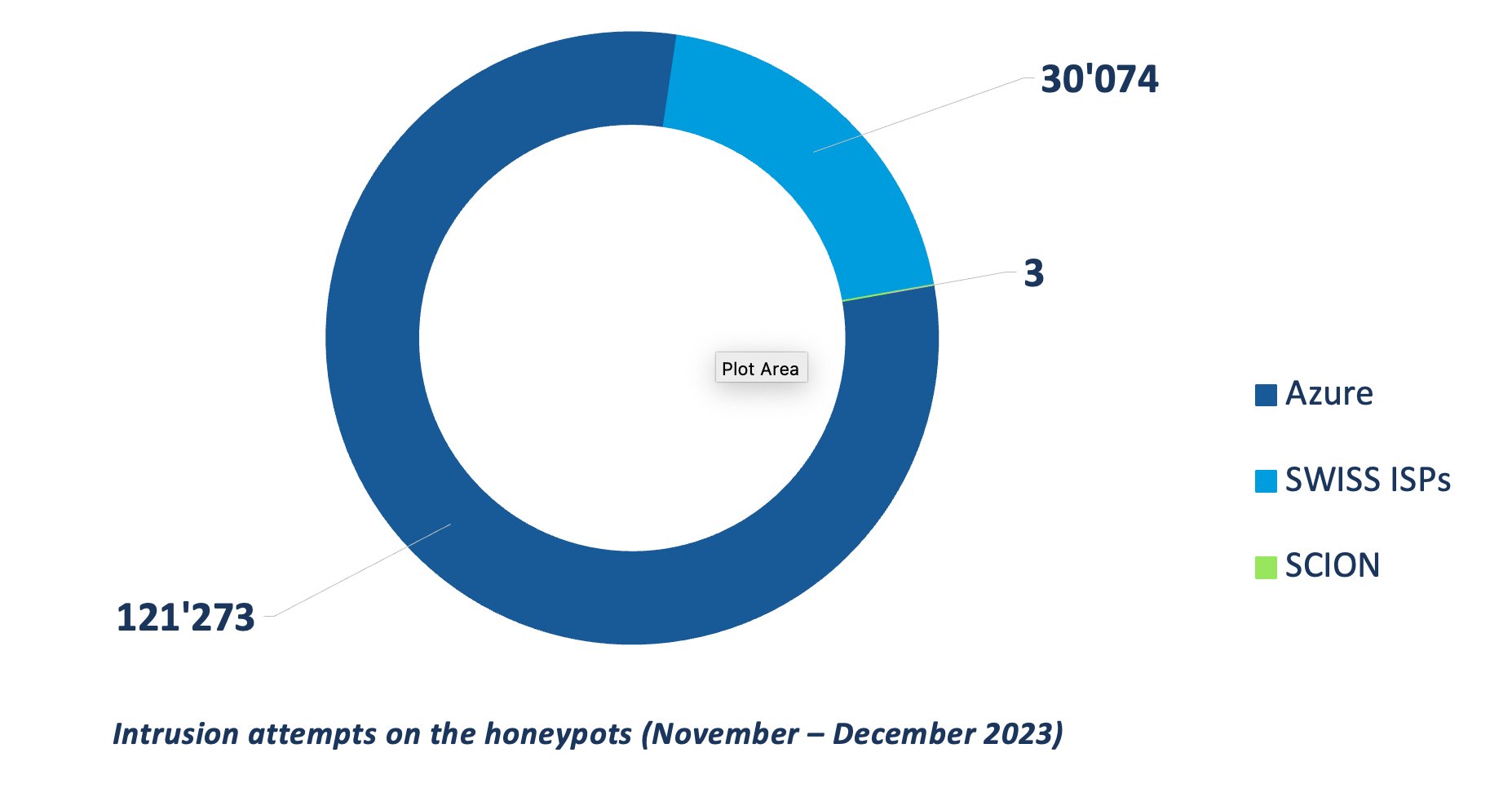
Source: Anapaya Systems AG
This table shows how those intrusion attempts translate across services (SSH vs. telnet). What is interesting here is that between Azure and the Swiss network, telnet incidents are comparable which indicates that the hackers are probably aware that honeypots are being used as a tactic in such instances.
| Honeypot network | ssh > intrusion attempts | telnet > intrusion attempts |
| Azure | 111’846 | 9’427 |
| Swiss ISPs | 22’829 | 7’245 |
| SCION | 1 | 2 |
Source: Anapaya Systems AG
Reduced attack surface on SCION versus Swiss residential network
Breaking it down, we can also see where the malicious activities’ IP addresses originate. Most of them come from China, Canada, United States and Singapore. Few come from Switzerland, ergo the attack surface could be significantly reduced if you limit network access to Switzerland. Yet, we still see a big difference in intrusion attempt from within Switzerland: on SCION are 3 and on the Swiss network are 30k. If we look at the IP addresses of the malicious actors, we see that only 207 IP addresses originated in Switzerland whereas the remaining 151k+ IP addresses came from elsewhere.
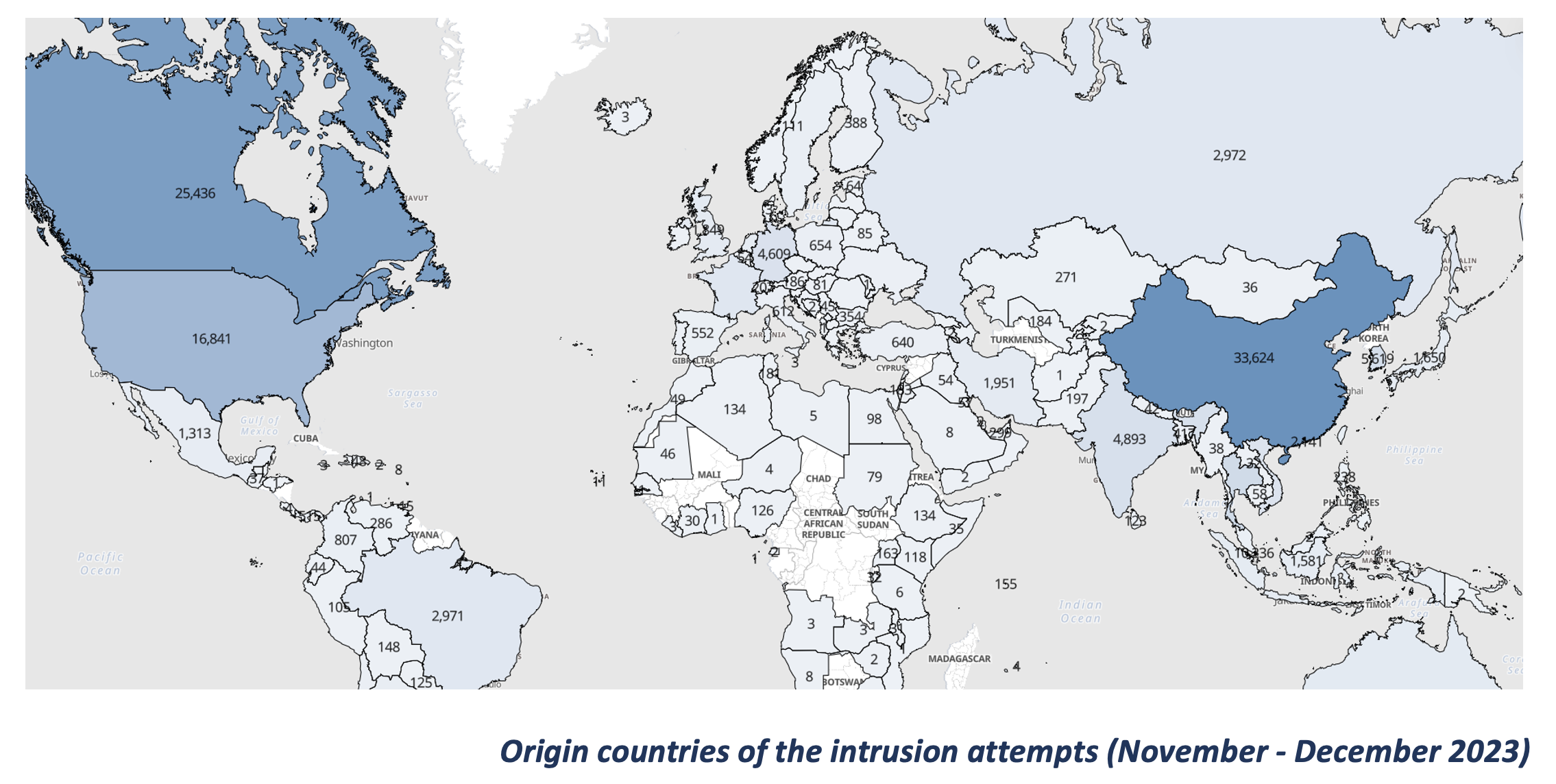
Source: Anapaya Systems AG
Lessons learned: be strategic and minimize your attack surface
While it is difficult to pinpoint a business’s precise attack surface, practically speaking: the bigger your network the larger the risk. Easiest way to reduce that risk? Be strategic with your network. Looking at the face of most business use cases, they do not need to be accessible to everyone on the planet – not even remotely.
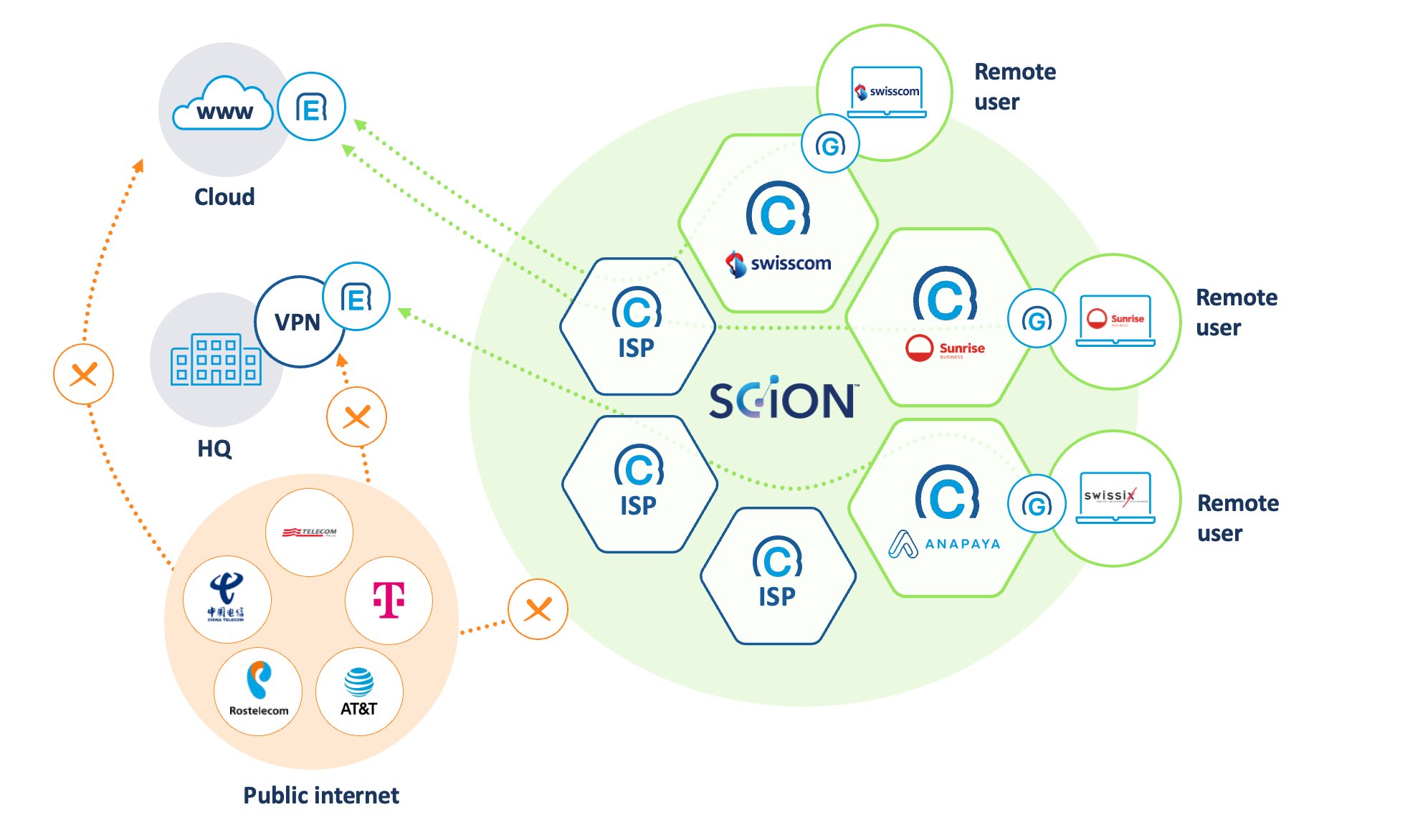
Source: Anapaya Systems AG
SCION’s architecture requires organizations to rethink and redesign their networks, with emphasis on geographical jurisdiction. Strategically decide what services can be seen by everyone and what to make visible only to selected ISPs and their remote users on SCION. The fact that surface risk is so much smaller on SCION (compared both to Azure and the Swiss network) means you can allocate more resources to the threats that still find a way through. In short, it is easier and more cost-efficient to monitor and follow up on 3 hits than it is for 30,000 or even worse 121,000.
Use cases fit for SCION
SCION is a robust solution, but you also need to think if it is a match for your business. If SCION is the safe path that you need your business to take, the map to help you navigate it is Anapaya. You can secure your critical service – be it an IoT service, a website, or VPN – within the SCION network by leveraging Anapaya EDGE, and then allow only the traffic from selected SCION-abled ISPs to access these services through Anapaya GATE. Watch the recording of this year's InfoGuard Innovation Day to find out more about this innovative solution!
Reducing attack surface makes your risk of malicious attacks more manageable, ensuring peace of mind and making it easier for cybersecurity professionals like us to react quickly to signals. Business continuity and data security are also prioritized, via DDoS and intrusion attack prevention. People cannot attack what they cannot see.
Managed SCION-Edge by InfoGuard
Anapaya combines the security of private networks with the flexibility of the Internet. The solution enables organisations to connect users, partners and customers to their applications and resources in a more reliable, efficient, and secure way than ever before. The connection between your infrastructure and the SCION network provider is ensured by the InfoGuard Service Edge as a "SCION network gateway". The InfoGuard Managed Service is based on a hardware switch from Extreme Networks with a virtual machine installed on it, on which the Anapaya SCION Router Engine is implemented and operated. Interested? Get in touch with us!
Blog

Risiko Schatten-KI: In 4 Schritten zur sicheren KI-Nutzung nach ISO 42001

NIS2, CRA, KRITIS und der 6. März: Jetzt zählt die nachweisbare Umsetzung!



