InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Strengthen your defences – protecting the web and cloud is essential

Don’t give viruses a chance – even at this time when so many are working from home – you need to strengthen your web and cloud defences! The web is growing and evolving at a rapid pace, but unfortunately the same is true for web-based malware which threatens and attacks end devices and important data. You need to keep your finger on the pulse and your eyes open for the latest cybercriminal trends. So how do you go about protecting yourself against the latest web threats? How does working from home affect your web and cloud protection? In this blog article, you’ll learn how your business can maximise web and cloud security.
The web and its insidious dangers
Currently, web threats are varied and they manifest themselves in many different forms. For example, ransomware arrives in a variety of different ways – as links in spam and phishing emails, “malvertising” and social media articles, and in what appear to be genuine files that your employees use every day. 70 to 90 % of all malware types have been customised to fit the company under attack! At the same time, the current obligation to work from home has fundamentally changed the way we live and work. Companies have had to adapt to the fact that most of their employees are working from home. This sometimes also affects the use of cloud services. To help understand the impact of working from home on the adoption and use of cloud services, our partner McAfee has been anonymously collecting cloud data from over 30 million cloud users around the world, over the period from January to April 2020. Here are the most important facts:
-
The use of cloud services is generally increasing There was a 50% increase in cloud usage across all industries, with the highest growth seen in manufacturing (+144%) and education (+114%).
- The strongest growth is in collaborative services
The use of cloud-based collaboration services in companies has more than doubled since the beginning of the year, which is hardly surprising. Zoom (+350%), Microsoft Teams (+300%) and Slack (+200%) have recorded particularly significant increases.
- The use of cloud enterprise services on non-managed devices
Cloud traffic from non-managed devices has doubled across all industries. When these devices access cloud services remotely from the corporate network, it increases the attack surface, so to prevent data leakage, you need be able to control cloud access by device type.
The cloud is in the cybercriminals’ sights
Unfortunately, in recent months there has also been a massive increase in the number of threats from external forces that specifically target cloud services. Collaboration services such as Microsoft 365 have been the most targeted. These external threats can be divided into two categories, with stolen credentials being the most common:
- Excessive use in unusual locations
The attack starts with a log-in from a location that is unusual or new to this company user. The attackers can retrieve large amounts of data or access privileged data. - Suspicious Superhero
Multiple login attempts are made from different locations that are geographically far from each other and in places that would be impossible to get to one after the other. For example, it really stands out when a user logs on to Microsoft 365 in Singapore, and just five minutes later logs on to Slack in California.
According to McAfee’s research, there has been no change in the categories for internal and insider threat, and that is certainly very encouraging, because it indicates that employees are not turning into criminals and stealing more data because they are working from home. Most attacks are external, cloud-native attacks that directly target cloud accounts.
Breakdown by industry: cloud threats
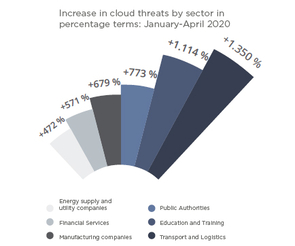 Industries have seen the biggest biggest growth areas in cloud account threats in transport and logistics, education and government. These industries have increasingly turned to cloud services to maintain their productivity. The attackers have repositioned themselves and attempt to compromise cloud accounts and steal data.
Industries have seen the biggest biggest growth areas in cloud account threats in transport and logistics, education and government. These industries have increasingly turned to cloud services to maintain their productivity. The attackers have repositioned themselves and attempt to compromise cloud accounts and steal data.
Source: McAfee report on cloud use and risks
To prevent all this happening, your business needs reliable web and cloud security solutions. So how do you manage to “master” this situation?
Our recommendations
Device and cloud security controls play a key role in providing security for staff who are working remotely. A cloud-native approach to security gives you the widest possible coverage, including for devices outside the network, enabling direct connections to cloud services. The following steps can help you achieve cloud-native security:
- The implementation of a cloud-based web gateway to protect enterprise devices from web-based threats, without having to route traffic via VPN.
- Employee access to approved cloud services from corporate devices with no need for a VPN, with data protected by a CASB (Cloud Access Security Broker).
- Policies defined within the CASB to ensure that cloud services have device checks and data controls, and are protected from attackers accessing SaaS accounts via the Internet.
- The implementation of multi-factor authentication for approved cloud services (wherever possible) to minimise the risk of credential theft.
- Employee access to SaaS enterprise applications using private devices to maintain productivity, while only allowing access to confidential data in the cloud on an “as-needed” basis.
The customised security solution
With McAfee Web Protection you are get protection from every direction. McAfee offers a transparent solution – each minute, McAfee Labs identifies an average of over 300 new malware variants. That’s around five per second. What this means for you is customised web security, either in the cloud, on the premises or as a hybrid solution.
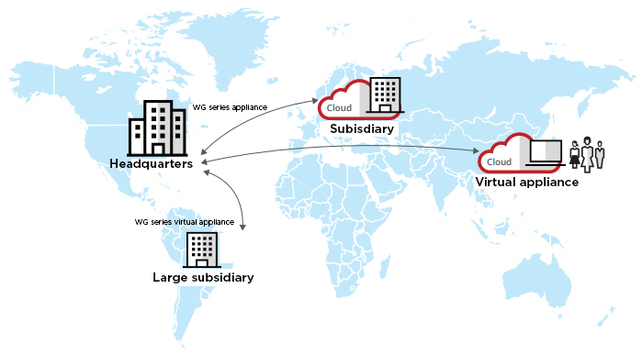
Figure – from McAfee Web Protection data sheet
McAfee Web Protection provides web filtering and malware scanning, as well as in-depth content scanning and detailed control over the use of cloud applications. Whether you want control via an on-premise solution, you value the unlimited scalability of a cloud service, or you use a hybrid combination of both, you can implement web security that meets both your current and future needs.
What are known as zero day attacks are also one of the current web threats. These happen particularly quickly – i.e. on the same day (zero day) that the vulnerability is discovered. Every hacker dreams of successful zero-day attacks, because they guarantee instant glory. McAfee Web Protection uses a patented approach to zero-day malware protection that includes machine learning. McAfee Web Protection scans active website content, mimics its behaviour in real time and forecasts its intentions. This gives you preventive protection against zero-day and targeted attacks before the threats are able to reach your endpoint systems.
There are a few pitfalls on the way to the cloud
Do you know which cloud services are already being used within your company? In our experience, cloud services are often used for specific projects or are in use in departments without the IT department knowing anything about it. Our Cloud Access Audit provides you with full transparency and clearly shows the risks involved.

If you would like to know more about McAfee solutions, please contact us. Our McAfee experts are ready to advise you.
Image source: from McAfee Web Protection data sheet
Blog

NIS2, CRA, KRITIS und der 6. März: Jetzt zählt die nachweisbare Umsetzung!

ISMS nach ISO 27001 schnell implementieren? Ein Realitätscheck.


