What features do modern cloud environments need to offer? On one hand, they must be scalable, on the other hand, it must be possible to quickly ramp up or shut down services in order to react to customers' desires flexibly. Increasing numbers of companies are investing in their own effectiveness via contact applications, microservices and dynamic infrastructures. But at the same time, they are confronted with an unprecedented complexity in terms of the applications to be managed, and this complexity quickly affects security. This blog post will show you how to meet this challenge.
Following the dynamics in cloud security is difficult, but really understanding the dynamics is a real challenge. This is because, with increasingly powerful orchestration tools, resources are dynamically provided in the cloud. In the cloud there are basically two types of services: serverless computing – and microservices – not to be confused with the traditional infrastructure, platform and application-as-a-service. But what are serverless computing and microservices all about?
Microservices are like Lego bricks
Let's imagine that you recently went on holiday and you took some great shots. Now you want to edit them. Of course, you can do this yourself, or you can subscribe to a cloud service and call on the appropriate automated function. As a service user, you only need to know the URL, the retrieval parameters and the login data – the service provider will do the rest. This is exactly how the micro services concept works: loosely connected and self-contained functions can be put together like Lego bricks.
And what about if you're the service provider? In this case, you have a cloud-based stack of containers. In the individual containers, you operate infrastructures such as databases, message queues, and applications that are provided by your micro services. You have the advantage that you can move these containers around effortlessly – just like in a container port. Twistlocks are used to ensure that the containers are secured during transport in the hold of the giant container ships or when being transported by truck. You can find out exactly what twistlocks are below.
Traditional approaches to security get overwhelmed by the dynamic nature of cloud environments
But how can you ensure security in a system that is constantly evolving? A dynamic cloud environment poses the following significant challenges to a security solution:
- Tools for DevOps are used in the cloud for the purpose of continuous integration. A deployment should only take place where the defined (security) guidelines are adhered to.
- Containers and microservices running within them are stopped and started as required. This means that the security solution must be capable of dealing with dynamic behaviour. At the same time, a high degree of automation needs to be achieved.
- During runtime, the infrastructures should be checked for vulnerabilities and attacks prevented. Containers, cloud stacks and micro services must be protected during runtime. It is important to note that it is not enough to focus on one component. The cloud stack must be monitored at every level (host, virtualisation layer, containers, applications in the containers, microservices and networks).
Misconfigurations within cloud services create a major target for attacks
Seemingly simple misconfigurations within cloud services can quickly have serious consequences. One example is Docker Hub's loss of keys and tokens from 190,000 accounts. The culprit was a classic cyberattack in which the perpetrators exploited weak security configurations of the key and token storage within a cloud environment. The leak of over 13 million user records at Ladders is a perfect example of the serious consequences of a basic container misconfiguration.
Unit 42, our partner Palo Alto Networks' research team, investigated several areas: both the standard configuration practices within container platforms and in the public cloud, and the disclosure of information found in these containers. The results were published in the report "Misconfigured and Exposed: Container Services". This report provides interesting insights into containers that have been incorrectly configured, the methods for identifying services that are available to the public and what measures are available to protect container services.
Important precautions to minimise risk in container services
The Palo Alto Networks report proposes the following actions to improve the overall security of container platforms:
- Invest in cloud security platforms or managed services focusing on contact security strategies.
- Restrict access to services hosted on containers for internal networks through firewall controls or network policies for container platforms. The following links can facilitate secure access to containers:
- Docker – iptable-configuration
- Kubernetes – network guidelines
- Set basic authentication requirements for your containers. The two following links provide helpful instructions on how to set up a basic authentication procedure for Dockers or Cubernetes:
- Docker – Tokens
- Kubernetes – Authentication
- Identify the type of data stored or managed in the containers. Also, use appropriate security measures to keep these data types secure.
- Ensure that the compliance guidelines of your company help to define the necessary protective measures.
- Isolate the services to your own containers. Do not host more than one service on a single container. This will improve the resource efficiency of the container itself and contribute to putting in place effective security policies.
If you are using cloud services like these, we strongly recommend that you take these actions. They provide a solid foundation for protecting your container platform infrastructure from cyberattacks.
Twistlock for securing containers in the transport industry and cloud security
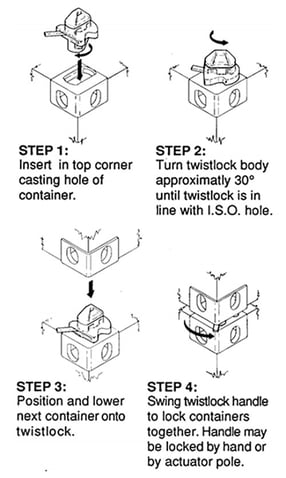
As mentioned previously, twistlocks are locks that connect containers to each other or the carrier vehicle. The twistlocks are inserted into the uniform corner fittings of the containers – or, to put it another way, the containers are placed onto the locks that are fixed to the vehicle. Then part of the twistlock is turned through 90 degrees to create a positive connection. The solution from "Twistlock", our partner in the field of cloud and DevOps security, can do much more than just that!
Twistlock provides an integrated solution to ensure and monitor container security. Unlike traditional methods, Twistlock fully integrates with continuous integration pipelines, such as Jenkins, and interacts natively with Docker or Kubernetes. The Twistlock framework is a vulnerability management suite for containers. Not only does it take care of the toughening of containers and images, but it also looks after the environment in which the containers run. In concrete terms, this means that Twistlock checks the containers for exploits, application or configuration errors, and monitors container activity. Twistlock detects security policy breaches, reports them and intervenes where necessary. Learn how Twistlock works in detail in this video.
The following table shows Twistlock's main features:
 |
Automation Scales security by automatically baselining the normal behaviour of an application, including communication with other cloud services. Based on this information, "Allow Rules" runtime models are generated. APIs are available for integration with existing tools. |
 |
Visibility Twistlock provides dynamic views of applications, components and security status. Vulnerabilities and compliance issues are assessed. Each host and container has a real-time "flight data recorder". |
 |
Prevention Twistlock makes it possible to automatically block abnormal behaviour of processes, network traffic and activities on files at runtime against the baseline. Only those applications classified as being compliant and from trusted sources are allowed. Twistlock enforces "Least Privilege" networking and micro-segmentation in your environment, thereby preventing proliferation of service accounts. |

Twistlock supports a wide range of cloud platforms, such as AWS, Azure, Docker EE, Google Cloud Platform, IBM Cloud, Kubernetes, OpenShift, Pivotal and Rancher. Would you like more details about Twistlock? Here you will find all information and details about the features of Twistlock (in german):
As you can see, Twistlock is indispensable, not only for securing metal containers during transport but also in cloud security. If you would like to find out more, please contact our experts:
Picture source Twistlock steps: https://gizmodo.com/the-simple-metal-mechanism-that-changed-the-global-econ-1530878459




